As more and more people use VPS for hosting their important online stuff, the risk of cyber trouble goes up. If someone sneaks in, it is not just about data—they can mess up the whole show. This article is all about why it is crucial to lock down your VPS and how Fail2Ban steps in as a superhero security solution.
Introducing Fail2Ban as a Security Solution
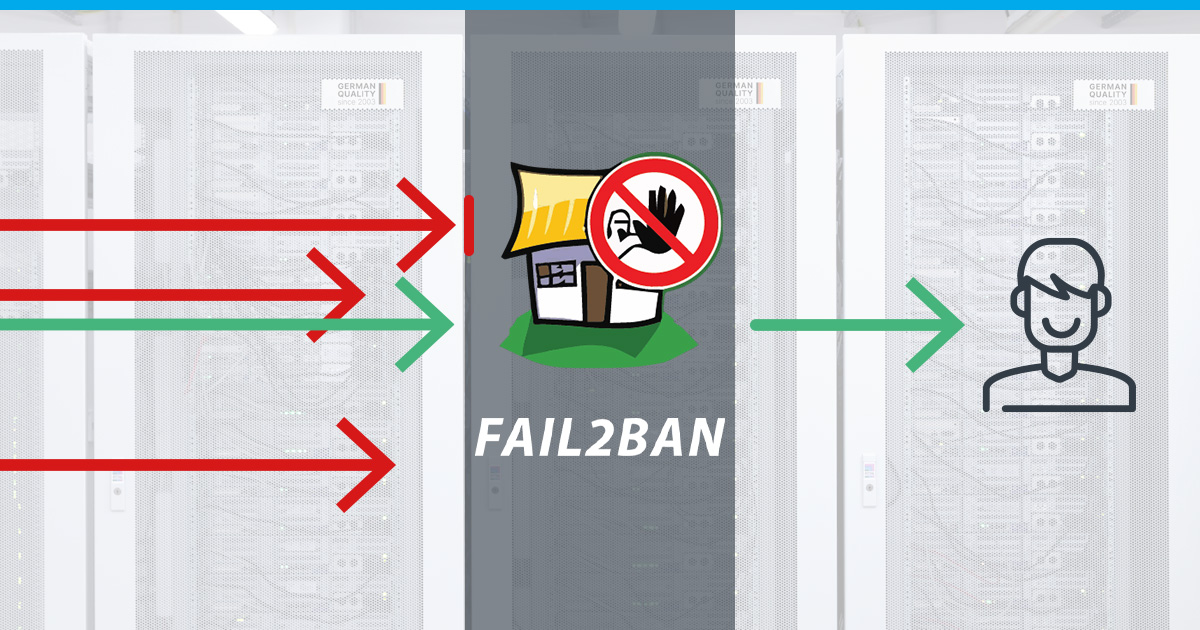
Fail2Ban is like your VPS bodyguard, always on the lookout for shady characters trying to break in. It is not your average security tool—it actively spots and fights off suspicious activity as it happens. Instead of sticking to old-school security, Fail2Ban adjusts on the fly to new threats, making it a tough shield for your VPS against all sorts of online trouble.
In the next parts, we will break down the basics of VPS security, get into the practical details of how Fail2Ban works, and walk you through setting it up on your virtual turf. This article is your guide to making your VPS a fortress against cyber threats. Get ready to dive in and see how Fail2Ban can level up your virtual security game.
Understanding Fail2Ban
In essence, Fail2Ban assumes the role of an ever-watchful custodian, carefully patrolling the digital boundaries of your VPS. Its open-source architecture is tailored to discern, analyze, and respond proactively to potential threats, making it an indispensable component in the arsenal against cyber vulnerabilities within your virtual infrastructure.
What is Fail2Ban?
Fail2Ban’s function, as an open-source utility, is primarily to discern and respond promptly to any anomalous activities within your VPS. Picture it as a digital sentinel stationed at the gates, monitoring and intervening upon detecting suspicious behavior.
How Does Fail2Ban Work?
Fail2Ban functions on a real-time detection and response paradigm. Upon identifying aberrations, such as repetitive failed login attempts or irregular network traffic patterns, it initiates responsive measures. Its adaptability to the ever-evolving threat landscape distinguishes Fail2Ban, rendering it an adept defender against an array of cyber threats.
Key Concepts of Fail2Ban: Jails, Filters, and Actions
To comprehend the operational dynamics of Fail2Ban, it is essential to acquaint yourself with key terminologies:
- Jails: These serve as designated security zones, segregating misbehaving IP addresses and restricting their potential harm.
- Filters: Formulating the rules of engagement, filters define patterns of behavior that prompt Fail2Ban to take action.
- Actions: When triggered by filters, Fail2Ban executes predefined responses—ranging from temporary bans to notifying administrators—tailored to uphold the integrity of the system.
In subsequent sections, we will delve further into these critical components, providing a comprehensive understanding of the nuanced workings of Fail2Ban. Prepare to unravel the sophistication behind your digital custodian.
How to Install Fail2Ban on a VPS
In this chapter, we dive into the practical aspect of fortifying your VPS by installing Fail2Ban—a pivotal step in bolstering your digital defenses.
Installing Fail2Ban on Debian-based Distributions
Whether you are on Debian or Ubuntu, the installation process for Fail2Ban on Debian-based distributions follows a similar, straightforward path. Begin by updating your package list with:
sudo apt updateThen, install Fail2Ban using the package manager, APT:
sudo apt install fail2banIn the upcoming sections, we will delve into the configuration of Fail2Ban, ensuring it aligns with your specific security needs. Get ready to fortify your VPS with an added layer of protection.
Basic SSH Protection Configuration with Fail2Ban
As we embark on configuring Fail2Ban for optimal security, our initial focus centers on fortifying SSH access—an integral entry point for many servers. This detailed walkthrough will guide you through fine-tuning Fail2Ban to protect against unauthorized SSH attempts. Following this, we will show you the practice of monitoring log files, providing insights into potential threats and essential tips for efficient log analysis.
Configuring Fail2Ban for SSH Protection
To customize Fail2Ban for robust SSH protection, begin by accessing the primary configuration file using your preferred text editor:
sudo nano /etc/fail2ban/jail.confWithin this file, locate the SSH section, commonly denoted as [sshd]. Here, specific parameters shape Fail2Ban’s response to suspicious SSH activities. Two critical settings to tailor are:
- maxretry: This parameter sets the maximum allowable login attempts before Fail2Ban intervenes. Customize this value based on your VPS security requirements.
- bantime: This parameter dictates the duration of the ban imposed on an IP address surpassing the defined maxretry. Adjust this duration to align with your security policies.
For instance, modifying the [sshd] section could look like this:
[sshd]
enabled = true
port = ssh
filter = sshd
logpath = /var/log/auth.log
maxretry = 3
bantime = 5mSave the changes and exit the editor. To apply the modifications, restart Fail2Ban:
sudo service fail2ban restartThis finely tuned configuration establishes a robust defense against SSH-based threats, setting the stage for further customization in subsequent sections.
Testing Fail2Ban
In this chapter, we engage in practical assessments to gauge the effectiveness of Fail2Ban in real-world scenarios. Through simulations and verifications, we will ensure your configuration stands resilient against potential threats.
Simulating Brute Force Attacks
To truly evaluate Fail2Ban’s prowess, we will simulate brute force attacks on your VPS. This involves intentionally generating multiple failed login attempts to trigger Fail2Ban’s response mechanism.
To simulate a brute force attack, try to login to your server via ssh with wrong passwords over and over again. After your defined “maxretrys”, you will be locked out of your server for the time you set in “bantime” (in our example, 5 minutes).
Observe how Fail2Ban responds to these simulated attacks and whether it accurately identifies and blocks the malevolent activities.
Verifying Fail2Ban’s Effectiveness
After simulating brute force attacks, it is crucial to verify whether Fail2Ban effectively mitigated the threats. Check Fail2Ban’s status and the corresponding logs to confirm if the simulated attackers are now banned.
Use the following command to view the status:
sudo fail2ban-client statusInspect the logs, typically located at /var/log/fail2ban.log, to ensure entries reflecting the banned IP addresses are present:
sudo cat /var/log/fail2ban.log | grep Ban This step-by-step verification process ensures that Fail2Ban not only detects but also responds appropriately to simulated threats.
How to Use Fail2Ban with Various Services
In this chapter, we extend the reach of Fail2Ban to safeguard additional services critical to your VPS environment. From protecting your MailCow mail server to fortifying Nextcloud, we will explore specific configurations tailored to enhance security across diverse applications.
Protecting MailCow Mailserver with Fail2Ban
Securing your MailCow mail server is paramount in safeguarding sensitive communication. To integrate Fail2Ban with MailCow, start by locating the relevant logs. Typically, MailCow logs are stored in /opt/mailcow-dockerized/mailcow.conf or /var/log/mail.log. Craft a custom filter for Fail2Ban to parse these logs and set up corresponding jails.
For example, create a new filter file, e.g., /etc/fail2ban/filter.d/mailcow.conf:
[Definition]
failregex = LOGIN authenticator failed for .+ \[<HOST>\]:.*
NOQUEUE: reject: RCPT from \[<HOST>\].* Auth failure: 535
Now, configure a jail in /etc/fail2ban/jail.local:
[mailcow]
enabled = true
port = smtp, submission, imap, imaps, pop3, pop3s
filter = mailcow
logpath = /opt/mailcow-dockerized/mailcow.conf
maxretry = 3
bantime = 3600Adjust the paths and parameters as per your MailCow setup. After saving the configurations, restart Fail2Ban:
sudo service fail2ban restartSecuring Nextcloud with Fail2Ban
Nextcloud, a collaborative platform, can be further fortified using Fail2Ban. Begin by identifying Nextcloud’s log location, usually found in the Nextcloud data directory or Apache/Nginx logs. Create a custom filter for Nextcloud in /etc/fail2ban/filter.d/nextcloud.conf:
[Definition]
failregex = Login failed.*REMOTE_ADDR=<HOST>
Next, configure a jail in /etc/fail2ban/jail.local:
[nextcloud]
enabled = true
port = http, https
filter = nextcloud
logpath = /path/to/nextcloud.log
maxretry = 3
bantime = 3600Ensure to customize paths and parameters based on your Nextcloud setup. Save the configurations and restart Fail2Ban.
Fail2Ban Best Practices
From routine updates and maintenance to synergizing with other security measures and the importance of regular backups, these best practices form a comprehensive approach to fortify your virtual environment:
Regularly Updating and Maintaining Fail2Ban
To maintain optimal security, keeping Fail2Ban up to date is crucial. Regularly check for updates and security patches to ensure you have the latest features and defenses against emerging threats. Execute the following commands to update and upgrade Fail2Ban on Debian-based systems:
sudo apt update sudo apt upgrade fail2ban Simultaneously, maintaining Fail2Ban involves monitoring logs, reviewing configuration settings, and adjusting parameters based on evolving security requirements. Regularly auditing your Fail2Ban setup ensures it remains an effective barrier against a dynamic threat landscape.
Combining Fail2Ban with Other Security Measures
While Fail2Ban serves as a robust security layer, its effectiveness can be enhanced by complementing it with other security measures. Consider deploying additional tools such as intrusion detection systems (IDS), firewalls, and security patches. A multi-faceted security approach reinforces your VPS against diverse cyber threats.
For instance, tools like ufw (Uncomplicated Firewall) can work in tandem with Fail2Ban to bolster network security. Install and configure ufw to limit access to essential services:
sudo apt install ufw
sudo ufw allow ssh
sudo ufw enableIntegrating Fail2Ban with such measures creates a comprehensive defense strategy, fortifying your VPS from various angles.
Regular Backups
Fail2Ban, while effective, is just one component of a comprehensive security strategy. Regular backups are indispensable for safeguarding your data and configurations. In the event of a security breach or system failure, backups enable swift recovery without compromising critical information.
Configure automated backup routines for your VPS, ensuring that both application data and system configurations are included. Tools like rsync or dedicated backup solutions can facilitate this process. Regularly test and validate the backup restoration process to guarantee its reliability when needed.
Conclusion
In wrapping up our exploration of Fail2Ban and its role in VPS security, let us take a closer look at the key takeaways.
Recap of Fail2Ban’s Role in VPS Security
Fail2Ban stands as a vigilant guardian for your VPS, actively responding to potential threats in real-time. Its adaptability to evolving security landscapes ensures it remains a versatile and dynamic component of your defense strategy. The ability to customize configurations empowers you to tailor its responses to the specific security needs of your virtual environment.
Strengthening Your VPS Security with Fail2Ban
The journey with Fail2Ban does not conclude with its installation. Regular updates and meticulous maintenance are imperative to ensure optimal security. Integrating Fail2Ban with firewalls and intrusion detection systems enhances your VPS’s defense, creating a multi-layered security approach. This, coupled with the tool’s inclusion in a comprehensive defense strategy, fortifies your virtual domain against diverse cyber threats.
Moreover, do not underestimate the importance of regular backups. They serve as a safety net, enabling swift recovery in the face of unforeseen challenges, ensuring the resilience of your VPS.
In navigating the complex landscape of VPS security, Fail2Ban is not merely a tool but a proactive ally. Stay informed about emerging security trends, implement best practices, and continually refine your security posture. As you do, you fortify your VPS against a spectrum of cyber threats, creating a resilient and secure digital environment.