
Have you ever wondered if that file you just transferred is truly safe from unwanted eyes? In the digital age, where data is as valuable as currency, the security of file transfers is more important than ever. Enter FTP, or File Transfer Protocol – a veteran in the world of data transfer that’s been around since the dawn of the internet. But in 2024, with cyber threats evolving at breakneck speed, is FTP still a secure option for your sensitive data?
In this comprehensive guide, we’ll peel back the layers of FTP security. We’ll explore how this protocol works, its vulnerabilities, and whether it’s still a viable option in today’s security-conscious digital world. Whether you’re a business owner concerned about data protection, an IT professional evaluating file transfer solutions, or just curious about online security, this article will equip you with the knowledge to make informed decisions about your file transfer needs.
Article Topics
- How FTP Works: An Overview of the File Transfer Protocol
- The Security Risks of Using File Transfer Protocol
- Secure Alternatives to File Transfer Protocol
- Why File Transfer Protocol is Still Used Despite Security Concerns
- When is File Transfer Protocol Secure Enough?
- Best Practices for Securing File Transfers
- Alternatives for Businesses Seeking Secure File Transfer Solutions
- Conclusion: Should You Still Use FTP in 2024?
How FTP Works: An Overview of the File Transfer Protocol
To understand the security implications of File Transfer Protocol, let’s first explore how it operates. This protocol, developed in the early days of the internet, follows a client-server model for transferring files.
Here’s a simplified breakdown of the process:
- Connection Initiation: Your computer (the client) reaches out to the server, typically on port 21.
- Authentication: You provide credentials – usually a username and password.
- Command Channel Establishment: Once authenticated, a command channel opens for sending instructions.
- Data Transfer Setup: When you request a file, a separate data channel opens, often on port 20.
- File Transfer: Data flows through this channel, either uploading or downloading files.
- Connection Closure: After the transfer, both channels close.
This process might seem straightforward, but it’s this simplicity that can lead to security vulnerabilities.
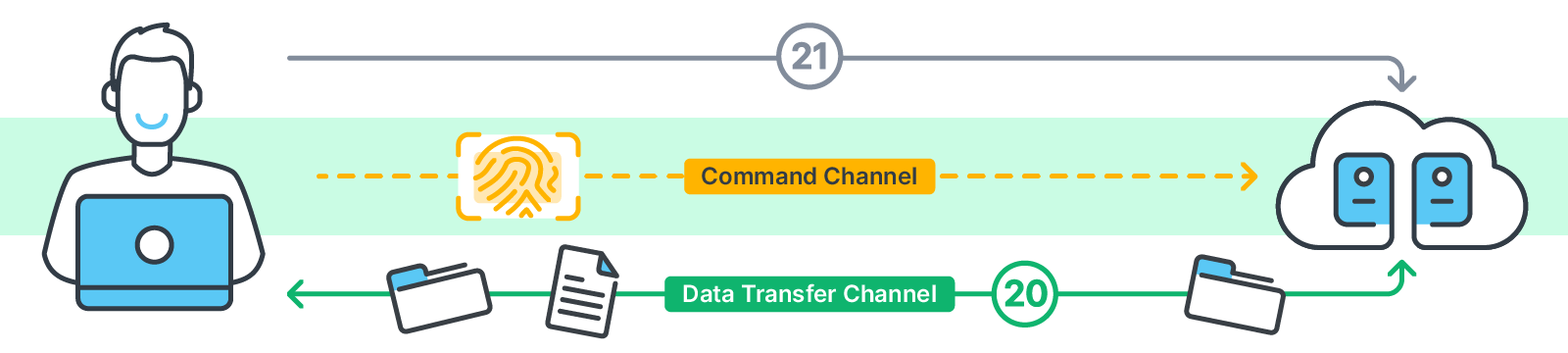
Key points to note about this protocol:
- It uses separate channels for commands and data.
- By default, it sends data, including login credentials, in plain text.
- It doesn’t inherently include encryption.
These characteristics, while making the protocol efficient and easy to implement, also open the door to potential security risks. In the next section, we’ll look into these vulnerabilities and why they matter in today’s digital landscape.
Remember, if you’re setting up a file transfer system on your Contabo VPS, VDS, or Dedicated Server, understanding these basics is essential for implementing proper security measures.
The Security Risks of Using File Transfer Protocol
While the simplicity of this protocol has contributed to its longevity, it also introduces several security concerns. Let’s examine the key vulnerabilities that make unmodified File Transfer Protocol a risky choice for sensitive data in 2024.
Unencrypted Data Transfers
The most glaring issue is the lack of encryption. When you send files or login credentials using this protocol, the data travels across the network in plain text. This means anyone intercepting the traffic can easily read the information, potentially exposing sensitive data or login details.
Vulnerability to Man-in-the-Middle Attacks
Without encryption, this protocol is susceptible to man-in-the-middle attacks. An attacker can intercept the connection between client and server, potentially altering the data in transit or injecting malicious content into the file transfer.
Password Theft and Account Compromise
Since login credentials are sent unencrypted, they’re vulnerable to interception. This could lead to unauthorized access to your server, potentially compromising not just your files but your entire system.
These vulnerabilities are particularly concerning in today’s landscape of sophisticated cyber threats and stringent data protection regulations. For businesses handling sensitive information or operating in regulated industries, using unmodified File Transfer Protocol could lead to severe consequences, including data breaches, regulatory fines, and loss of customer trust. It’s worth noting that while these risks are inherent to the basic protocol, there are secure alternatives and best practices that can mitigate these vulnerabilities.
In the next section, we’ll explore secure alternatives that address these vulnerabilities while still providing efficient file transfer capabilities.
Secure Alternatives to File Transfer Protocol
Given the security risks associated with traditional file transfer methods, several secure alternatives have emerged. These protocols address the vulnerabilities we discussed earlier while maintaining efficient file transfer capabilities. Let’s explore some of the most popular options:
SFTP (Secure File Transfer Protocol)
SFTP operates over the SSH protocol, providing a secure channel for file transfers. Key benefits include:
- Ability to resume interrupted transfers
- Encrypted data transfers
- Strong authentication methods
FTPS (FTP Secure)
FTPS adds a layer of SSL/TLS encryption to the traditional protocol. It offers:
- Option for implicit or explicit security
- Compatibility with existing FTP systems
- Data encryption during transfer
HTTPS for File Transfer
While primarily used for web browsing, HTTPS can also facilitate secure file transfers. Advantages include:
- Built-in encryption and authentication
- Widespread compatibility
- Firewall-friendly (uses standard port 443)
SCP (Secure Copy Protocol)
SCP, like SFTP, uses SSH for secure file transfers. It’s known for:
- Efficient for transferring large files
- Simplicity and ease of use
- Strong encryption
| Protocol | Encryption | Ease of Use | Compatibility |
|---|---|---|---|
| SFTP | High | Moderate | Good |
| FTPS | High | Moderate | Excellent |
| HTTPS | High | High | Excellent |
| SCP | High | High | Good |
Each of these alternatives offers significant security improvements over the traditional protocol. The choice between them often depends on specific needs, existing infrastructure, and technical expertise. Most modern server configurations, such as a Linux VPS from Contabo, support these options out of the box, allowing you to enhance your file transfer security with minimal effort.
In the next section, we’ll explore why, despite these secure alternatives, some organizations still use the traditional protocol, and under what circumstances it might be considered acceptable.
Why File Transfer Protocol is Still Used Despite Security Concerns
Despite the well-known security risks, the traditional file transfer protocol remains in use in various scenarios. Let’s explore the reasons behind its continued popularity:
Specific Use Cases:
In certain controlled environments, like closed networks or for non-sensitive data transfers, the basic protocol might be deemed sufficient.
Legacy Systems:
Many older systems and applications were built with this protocol in mind. Upgrading these systems can be costly and time-consuming, leading some organizations to stick with what they have.
Simplicity and Familiarity:
The protocol’s straightforward nature makes it easy to set up and use, especially for those who have been working with it for years.
Compatibility:
It’s widely supported across different platforms and operating systems, ensuring broad compatibility.
Performance:
For large file transfers within secure internal networks, the protocol can offer better performance due to less overhead compared to encrypted alternatives.
Pro Tip: Secure Alternatives
If you’re using the traditional protocol due to legacy systems, consider implementing a secure alternative like SFTP on your server. This allows you to maintain compatibility while significantly enhancing security.
It’s important to note that while the above reasons explain its continued use, they don’t justify using the unsecured protocol for sensitive data or in public networks. Organizations should carefully assess their needs and the risks involved before deciding to stick with this legacy protocol.
In the next section, we’ll explore scenarios where the traditional protocol might be considered secure enough, and what precautions should be taken in these cases.
When is File Transfer Protocol Secure Enough?
While we’ve discussed the security risks associated with the traditional file transfer protocol, there are scenarios where its use might be considered acceptable. Let’s explore these situations:
Internal Network Usage
Within a closed, internal network that’s properly secured from external access, using the basic protocol can be relatively safe. In this environment:
- The risk of external interception is minimized
- Network traffic is contained within the organization
- Additional security layers like firewalls provide protection
However, it’s important to ensure that your internal network is truly secure and isolated from potential threats.
Non-Sensitive Data Transfers
For transferring non-sensitive, publicly available data, the basic protocol might be sufficient. Examples include:
- Distributing public documents
- Sharing open-source software
- Updating website content that’s already public
In these cases, even if the data were intercepted, it wouldn’t pose a significant risk.
Pro Tip: Assessing Data Sensitivity
Always err on the side of caution when determining data sensitivity. If there’s any doubt, opt for a secure transfer method. It’s important to note that while these scenarios might justify using the basic protocol, they’re becoming increasingly rare in today’s security-conscious digital world. Most organizations are moving towards always-encrypted transfers as a best practice, regardless of the perceived sensitivity of the data.
In the next section, we’ll discuss best practices for securing your file transfers, whether you’re using the traditional protocol or more secure alternatives.
Best Practices for Securing File Transfers
Even if you’re using the traditional file transfer protocol, there are steps you can take to enhance security. Here are some best practices to consider:
Implement File Integrity Checks:
Use checksums or hash values to verify that files haven’t been tampered with during transfer.
Use Secure Alternatives:
Whenever possible, opt for secure protocols like SFTP or FTPS. These provide encryption and stronger authentication methods.
Implement Strong Authentication:
If you must use the basic protocol, enforce strong passwords and consider implementing two-factor authentication.
Limit Access:
Restrict file transfer access to specific IP addresses or ranges. This reduces the attack surface for potential intruders.
Regular Updates:
Keep your file transfer server software up-to-date to protect against known vulnerabilities.
Encrypt Sensitive Files:
Even when using secure transfer methods, encrypt sensitive files before transmission for an extra layer of protection.
Monitor and Log Activities:
Implement logging and regularly review logs to detect suspicious activities or unauthorized access attempts.
Use a Dedicated Transfer Server:
Consider setting up a dedicated server for file transfers, isolated from other critical systems.
Implementing these practices can significantly enhance the security of your file transfers, regardless of the protocol you’re using.
Remember, security is an ongoing process. Regularly review and update your security practices to stay ahead of evolving threats and ensure the safety of your data transfers.
Alternatives for Businesses Seeking Secure File Transfer Solutions
- Managed File Transfer (MFT) Solutions:
These platforms provide a centralized system for handling file transfers with features like:
- End-to-end encryption
- Detailed audit trails
- Automated workflows
- Integration with existing systems
- Cloud-based File Sharing Services
Services like Dropbox Business or Google Drive for Enterprise offer:
- Easy-to-use interfaces
- Robust security measures
- Collaboration features
- Automatic syncing across devices
- Virtual Private Networks (VPNs):
Using a VPN in conjunction with file transfer protocols adds an extra layer of security by:
- Encrypting all network traffic
- Masking your IP address
- Providing secure remote access
- Secure Web Applications:
Custom-built web applications can offer:
- Tailored security measures
- Integration with internal systems
- User-friendly interfaces for file uploads and downloads
Pro Tip: Hybrid Solutions
Consider combining a secure protocol like SFTP with a cloud service for a cost-effective, flexible solution that balances security and ease of use. When choosing an alternative, consider factors like:
- The sensitivity of your data
- Compliance requirements in your industry
- The technical capabilities of your team
- Integration needs with existing systems
- Budget constraints
Remember, the goal is to find a solution that not only secures your file transfers but also enhances your overall workflow and productivity.
Conclusion: Should You Still Use FTP in 2024?
As we’ve explored throughout this article, the traditional file transfer protocol has significant security vulnerabilities that make it a risky choice for many modern use cases. So, should you still use it in 2024? The short answer is: probably not, at least not without careful consideration and additional security measures.
Here’s a summary of key points to consider:
- Security Risks: The lack of encryption in the basic protocol makes it vulnerable to data interception and manipulation.
- Better Alternatives: Secure options like SFTP and FTPS offer similar functionality with added security features.
- Compliance Issues: Many industries have regulations that require secure data transfer, making the basic protocol non-compliant.
- Limited Use Cases: While there are scenarios where it might be acceptable (like internal networks or non-sensitive data), these are becoming increasingly rare.
- Best Practices: If you must use the traditional protocol, implementing strong security measures is essential.
The digital world has evolved significantly since the protocol’s inception. Today’s internet users expect and deserve secure connections for all their online activities, including file transfers. If you’re still using the basic protocol, now is the time to consider upgrading to a more secure alternative.
Remember, the security of your data isn’t just about protecting information – it’s about maintaining trust with your users, partners, and customers. By prioritizing secure file transfer methods, you’re not just following best practices; you’re investing in the long-term success and reliability of your digital operations.
