
Running a self-hosted Nextcloud instance gives you incredible control over your data, but that freedom comes with a critical responsibility: security. While Nextcloud is built with safety in mind, its default state is just a starting point. Truly protecting your server from threats requires a proactive approach. This comprehensive Nextcloud security guide is designed for administrators ready to go beyond the basics. We will cover essential Nextcloud hardening techniques to transform your server into a fortified private cloud. Following these steps is a vital part of ensuring robust Nextcloud security and safeguarding the integrity of your data.
Why Your Nextcloud Server Security is Your Responsibility
When you decide to self-host an application like Nextcloud, the responsibility for securing it shifts entirely to you. Unlike commercial cloud services that handle security in the background, a private server requires the administrator to take active measures to protect it. This Nextcloud administrator guide is based on that fundamental idea: effective security is an active process, not a default state. Every setting you configure contributes directly to your defense against potential threats.
A commitment to proper Nextcloud server security is a continuous process of management and upkeep. While a strong hardware foundation is important, such as the optimized servers used for our Nextcloud Hosting, the security of the software and the user data it holds is ultimately managed by the administrator. Acknowledging this responsibility is the critical first step in maintaining a secure private cloud.
Foundational Security: Operating System and Deployment Best Practices
Effective Nextcloud security begins at the operating system level, long before a user ever logs in. The choices you make during server setup and deployment create the foundation upon which all other security measures are built. A secure Nextcloud deployment involves hardening the OS, isolating data, and enforcing strict file permissions.
Harden Your Operating System
Your server’s operating system is the first line of defense. Keep it lean and secure with these practices:
- Regular Updates: Consistently apply all system and package updates to patch known vulnerabilities. Run sudo apt update && sudo apt upgrade regularly.
- Use a Firewall: Implement a firewall like UFW to block all non-essential ports, allowing traffic only for necessary services like SSH and HTTPS.
- Mandatory Access Control: Ubuntu uses AppArmor by default, which confines programs to a limited set of resources. For administrators familiar with other systems, this is conceptually similar to Nextcloud SELinux policies. Ensure AppArmor is active and running with the default profiles to significantly limit the potential damage from a compromised application.
Isolate Your Data Directory from the Web Root
One of the most critical security configurations is the location of your data directory. Never place the Nextcloud data directory inside the web root. Placing the data folder within the web-accessible directory (e.g., inside /var/www/html/) is a severe risk. A minor web server misconfiguration could expose all your user data directly to the internet. The correct approach is to define the data directory in a location outside the web root, for instance, in /var/nextcloud-data, making it inaccessible via direct web requests.
Enforce Strict File Permissions
The principle of least privilege should govern your Nextcloud file system. The web server user (www-data on Ubuntu) needs specific permissions to run Nextcloud, but these should be as restrictive as possible. After installation, ensure the ownership of your Nextcloud directories is set correctly. The www-data user must be the owner of the config, apps, and your designated data directory to manage configuration, apps, and user files. While more complex permission schemes are possible, ensuring correct ownership and isolating the data directory are the two most impactful steps for securing the file system of your deployment.
Securing Nextcloud Access: Authentication, HTTPS, and HSTS
Once the server’s foundation is secure, the next priority is to protect the pathways into your Nextcloud instance. This involves managing how users authenticate and ensuring the connection itself is always encrypted and trustworthy. We will also configure the server to instruct browsers to enable their own security features, creating a robust defense from the server all the way to the end-user’s screen.
Enforce Strong Authentication Policies
Weak or reused user passwords are a common entry point for unauthorized access. As an administrator, you can significantly mitigate this risk by enforcing strong password policies directly from within Nextcloud. Navigate to the “Security” section in your administration settings to configure these rules:
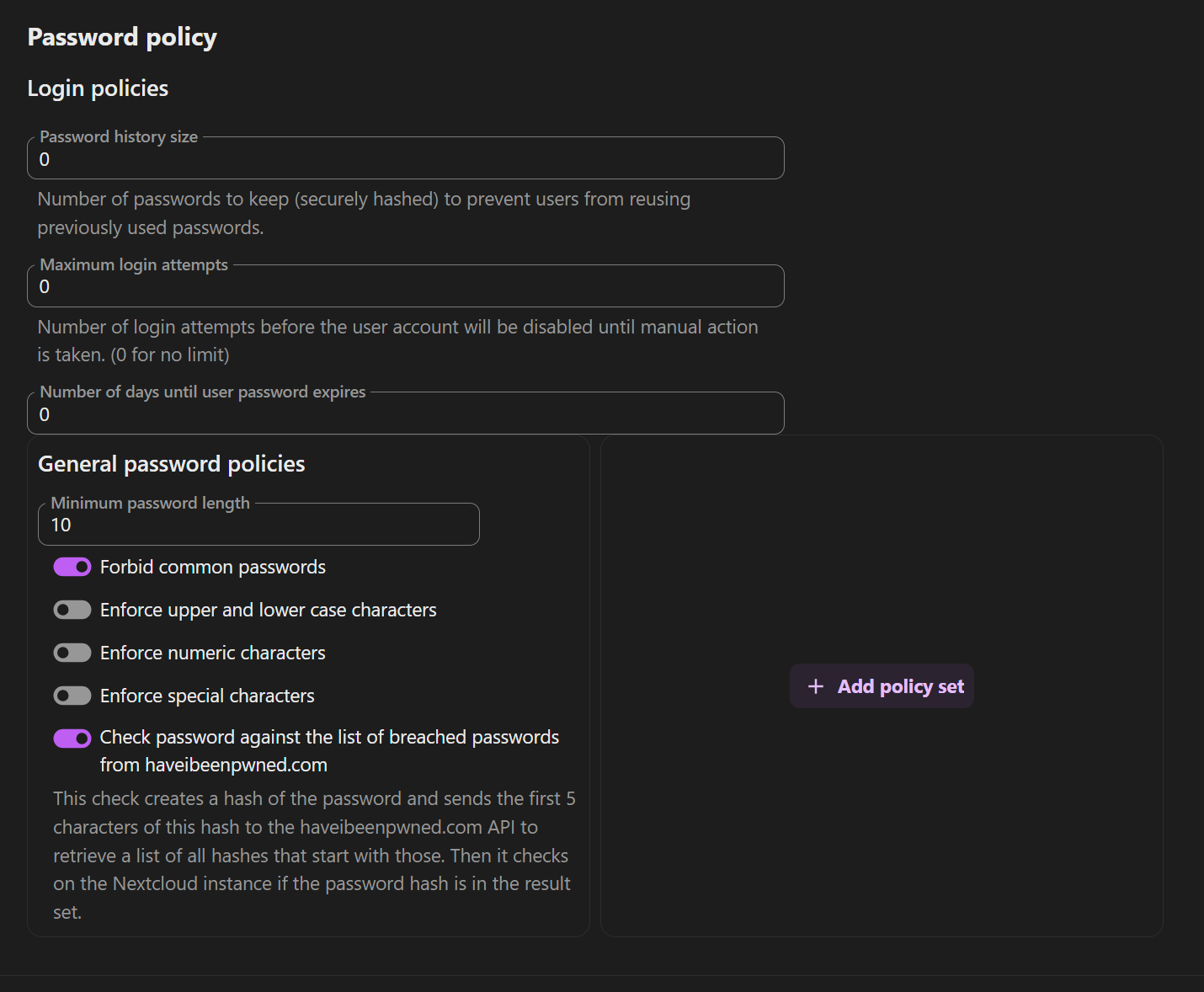
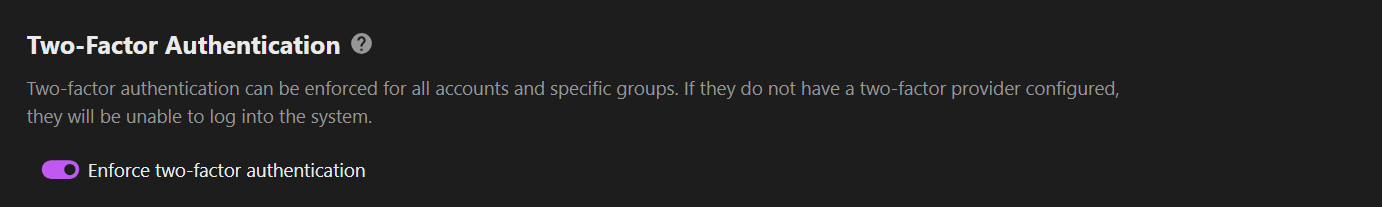
A good starting point is to enforce a minimum Nextcloud password length of at least 12 characters and require a mix of uppercase letters, lowercase letters, numbers, and special characters. For an even higher level of security, strongly encourage or mandate the use of Two-Factor Authentication (2FA) for all users:
Mandate Encrypted Connections with HTTPS and HSTS
Using Nextcloud https is a fundamental requirement for security, but we can significantly strengthen it by adding security headers. These headers are instructions your server sends to the user’s browser, telling it to behave in a more secure way.
- Locate your SSL configuration file. When you used Certbot, it created a specific configuration file for your domain’s HTTPS connection, typically located at /etc/apache2/sites-available/your-domain-le-ssl.conf.
- Open the file using the nano text editor. Remember to replace your-domain with your actual domain name.
sudo nano /etc/apache2/sites-available/your-domain-le-ssl.conf- Add the security headers. Inside the file, look for the <VirtualHost *:443> block. Anywhere within this block, add the following lines. This block includes HSTS and other important Nextcloud security headers.
Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains"
Header always set X-Content-Type-Options "nosniff"
Header always set X-Frame-Options "SAMEORIGIN"
Header always set Referrer-Policy "no-referrer"- Strict-Transport-Security (HSTS): This prevents downgrade attacks by telling browsers to only ever communicate with your server using HTTPS.
- X-Content-Type-Options: Prevents attacks where malicious scripts are disguised as other file types.
- X-Frame-Options: Blocks your Nextcloud site from being embedded in an iframe on another website, which is the primary defense against “clickjacking.”
- Referrer-Policy: Enhances user privacy by preventing the browser from sending referrer information to other sites when users click on links.
- Save and close the file. In nano, press CTRL+X, then Y, and finally Enter.
- Test and reload Apache. First, check your Apache configuration for syntax errors.
sudo apache2ctl configtestIf you see “Syntax OK,” safely reload Apache to apply the new headers.
sudo systemctl reload apache2Your server will now enforce secure connections, adding another critical layer of security.
Use a Dedicated Domain for Nextcloud
A final, critical best practice is to use a dedicated domain for Nextcloud. This means running your instance on a subdomain, like cloud.yourdomain.com, instead of in a subdirectory, like yourdomain.com/nextcloud.
The reason for this is security isolation. Browsers use a “Same-Origin Policy” to prevent websites from interfering with each other. If you run Nextcloud on the same domain as another application, like a blog, a vulnerability in that blog could potentially be exploited to interact with Nextcloud’s data or steal session cookies. By placing Nextcloud on its own dedicated domain, you create a strong security boundary, isolating it from vulnerabilities in any of your other web applications.
Mitigating Automated Attacks: Fail2ban and IP Restrictions
Your Nextcloud server, once public, will inevitably be targeted by automated bots attempting to guess user passwords. This is a constant threat known as a brute-force attack. You can proactively defend against this by implementing tools that automatically block malicious actors and by restricting who can access your server.
Block Brute-Force Attempts with Nextcloud Fail2ban
Fail2ban is an essential security tool for any internet-facing server. It actively scans log files and temporarily bans IP addresses that show malicious signs, such as too many password failures. Setting up Nextcloud fail2ban involves configuring Nextcloud to log failed attempts and then telling Fail2ban how to read that log.
- Install Fail2ban. If you don’t have it on your server yet, install it with apt:
sudo apt install fail2ban -y- Configure Nextcloud Logging. You need to tell Nextcloud to log failed login attempts to a specific file. Edit your config.php file:
sudo nano /var/www/html/nextcloud/config/config.php Add the following lines before the final ); in the file:
'log_type' => 'file',
'logfile' => '/var/log/nextcloud/nextcloud.log',
'loglevel' => 2,Now create the log file and give the web server ownership of it:
sudo mkdir /var/log/nextcloud
sudo touch /var/log/nextcloud/nextcloud.log
sudo chown -R www-data:www-data /var/log/nextcloud- Create the Fail2ban Jail. This tells Fail2ban which log to monitor and how to act. Create a new configuration file for Nextcloud:
sudo nano /etc/fail2ban/jail.d/nextcloud.local Paste the following configuration into the file. This configuration will ban an IP for one day after 3 failed login attempts.
[nextcloud]
enabled = true
port = http,https
filter = nextcloud
logpath = /var/log/nextcloud/nextcloud.log
maxretry = 3
bantime = 86400- Create the Fail2ban Filter. The filter tells Fail2ban what a failed login looks like in the log file. Create the filter file:
sudo nano /etc/fail2ban/filter.d/nextcloud.conf Paste the following regular expression into this file:
[Definition]
failregex = ^{"reqId":".*","level":2,"time":".*","remoteAddr":".*","user":".*","app":"core","method":".*","url":".*","message":"Login failed: '.*' (Remote IP: '<HOST>')".*}$- Restart and Verify. For the changes to take effect, restart Fail2ban.
sudo systemctl restart fail2ban You can check that the jail is active with:
sudo fail2ban-client status nextcloud Restrict Access with IP Whitelisting
For servers that should only be accessible to a few people from specific locations (like a home or office), the most effective security measure is to restrict access to a list of approved IP addresses. You can restrict Nextcloud admin ip access, or even all access, at the web server level. This prevents anyone not on the list from even reaching the Nextcloud login page.
To do this, edit your Apache SSL configuration file again:
sudo nano /etc/apache2/sites-available/your-domain-le-ssl.conf Inside the <VirtualHost *:443> block, add the following section. Replace the example IP addresses with your own trusted public IPs. You can add multiple Require ip lines.
<Directory /var/www/html/nextcloud>
Require ip 123.45.67.89
Require ip 98.76.54.32
</Directory>After saving the file, test your Apache configuration and then reload the service.
sudo apache2ctl configtest
sudo systemctl reload apache2 This is a highly restrictive measure, but for a truly private server, it’s one of the best ways to eliminate unauthorized access attempts.
Advanced Application-Level Security: Previews and Debug Mode
Beyond server and connection hardening, several settings within Nextcloud’s configuration file can be adjusted to reduce your attack surface and prevent potential information leaks. These Nextcloud config php security tweaks are simple to implement but have a significant impact on the overall security of your instance.
Reduce Attack Surface by Disabling Previews
Nextcloud automatically generates previews and thumbnails for many file types, such as images and videos. While this is a useful feature, the underlying software libraries used for this process (like ImageMagick) are complex and have historically been a source of security vulnerabilities. For high-security environments where previews are a non-essential feature, you can completely disable Nextcloud previews to reduce your server’s attack surface. This means the server will not execute this code at all, eliminating any associated risk.
To disable previews, edit your configuration file:
sudo nano /var/www/html/nextcloud/config/config.php Add the following line anywhere within the configuration array:
'enable_previews' => false,Save and close the file. This is a trade-off between functionality and security, but it is an effective hardening step.
Disable Debug Mode in Production
Debug mode is a tool for developers that provides highly detailed error messages. These messages are useful during setup or troubleshooting, but they are extremely dangerous on a live production server. If an error occurs, debug mode can leak sensitive information like server file paths, database details, and software versions. An attacker can use this information to stage a more effective attack.
You must ensure that debug mode is always turned off in your production environment. To verify this, check your configuration file:
sudo nano /var/www/html/nextcloud/config/config.php Look for the debug setting and make sure it is set to false:
'debug' => false,If this line does not exist, it defaults to false, which is secure. If it is set to true, change it immediately.
Conclusion
Following this Nextcloud hardening guide, you have systematically transformed a standard Nextcloud installation into a securely configured, production-ready server. You’ve hardened the operating system, secured the web server and browser connections, implemented automated defenses against brute-force attacks, and fine-tuned application-level settings to reduce the attack surface. Each layer of security you’ve added contributes to a robust defense for your private cloud.
However, the most important takeaway is that security is not a one-time task. The digital landscape is constantly evolving, and so are the threats. A secure server today may be vulnerable tomorrow if it is not maintained. True Nextcloud security maintenance is an ongoing process of vigilance. This includes regularly updating Nextcloud and its apps, keeping the server’s operating system and packages patched, and staying informed about new security best practices. By committing to these ongoing practices, you ensure that your self-hosted cloud remains a safe, private, and trustworthy place for your data.
Nextcloud Security FAQ
How often should I check for updates?
You should get into a routine of checking for operating system updates at least weekly. For Nextcloud itself and its applications, check for updates at least once a month. However, if a critical security vulnerability is announced, you should apply the patch as soon as possible.
Is Fail2ban enough to stop all brute-force attacks?
Fail2ban is highly effective at stopping simple, automated brute-force attacks from a single IP address. However, it may not stop a slow, distributed attack coming from thousands of different IPs. It should be seen as one essential layer in your defense, combined with strong passwords and Two-Factor Authentication.
My Nextcloud security scan shows warnings. What should I do?
The security scan found in the administration settings is an excellent tool. Don’t panic when you see warnings. Read each one carefully, as they are designed to be helpful. Many of the common warnings, such as those about missing security headers, were resolved by following the steps in this guide. For any others, the warnings often link directly to the official Nextcloud documentation explaining how to fix the issue.
Will disabling file previews damage my files?
No, disabling previews will not harm your original files in any way. This setting only prevents the server from generating thumbnails and small preview images. Your files can still be downloaded and viewed perfectly. The only change is a less visual experience when browsing files in the web interface.
Is it safe to install apps from the Nextcloud App Store?
You should exercise caution. While the app store provides incredible functionality, many apps are created and maintained by community developers, not the core Nextcloud team. Before installing an app, check when it was last updated, review its ratings, and see if it has an active development community (for example, on GitHub). Every app you add increases the potential attack surface of your instance, so only install apps that you need from trusted sources.
