
Imagine having complete control over your email communications – no more relying on third-party services that limit customization or compromise privacy. Setting up your own Linux mail server puts you in the driver’s seat, offering unparalleled flexibility and security. Whether you’re managing a business that demands airtight data control or a developer looking to experiment with custom configurations, this guide walks you through every step to setup mail server solutions that work for you.
At its core, a Linux mail server relies on three key protocols:
- SMTP (Simple Mail Transfer Protocol) handles sending emails, acting like a digital postal service.
- POP3 (Post Office Protocol) and IMAP (Internet Message Access Protocol) manage email retrieval, functioning as your personal mailbox handlers.
Why choose Linux? It’s open-source, cost-effective, and endlessly adaptable. Pair it with a Virtual Private Server (VPS) from Contabo, and you’ll tap into NVMe storage speeds that keep your email delivery fast and efficient.
You might wonder, “Why go through the effort when third-party services exist?” The answer lies in control. Self-hosting lets you tailor spam filters, encrypt communications your way, and ensure compliance with regional data laws.
This guide isn’t just about technical setup – it’s about empowering you to build an email system that grows with your needs. We’ll demystify terms like Postfix and Dovecot, simplify encryption with Let’s Encrypt, and even show you how to squash spam using tools like SpamAssassin. By the end, you’ll have a fully functional mail server and the confidence to maintain it.
Ready to ditch generic email services and craft a Linux mail server solution that’s truly yours? Let’s begin.
What is an SMTP Server?
Ever sent an email and wondered how it travels across the internet? That’s where SMTP (Simple Mail Transfer Protocol) comes in. Think of SMTP as your digital postal service – it handles the routing and delivery of every email that leaves your server.
Two major players dominate the Linux SMTP server landscape: Postfix and Sendmail. While Sendmail pioneered email delivery on Unix systems, Postfix has emerged as the modern choice for good reasons. Its modular design keeps different processes separate, reducing security risks and making troubleshooting straightforward.
When you run SMTP on a VPS with NVMe storage, you get lightning-fast email processing. Every time someone hits “send,” the message flows through several stages:
- Authentication checks verify the sender
- Content scanning looks for potential threats
- Queue management prepares messages for delivery
- Routing determines the fastest path to the recipient
The beauty of running your own SMTP server is that you get complete control over this entire process. You decide how strict your spam filters are, which encryption methods to use, and how to handle different types of messages.
Linux Mail Server Components
Building a mail server is like assembling a well-oiled machine – each component plays a vital role in handling your email traffic. Three main parts work together to make email magic happen: MUA, MTA, and MDA.
Your Mail User Agent (MUA) is the front-end interface where users read and compose emails. This might be Thunderbird on your desktop or Roundcube in your web browser. It’s the friendly face of your email system, handling the day-to-day tasks of reading, writing, and organizing messages.
Behind the scenes, the Mail Transport Agent (MTA) manages the complex job of routing emails to their destinations. When you click “send,” your MTA springs into action, determining the best path for your message and ensuring it reaches the correct server. This is where Postfix shines, offering better security and easier maintenance than traditional options.
The Mail Delivery Agent (MDA) acts as your personal mail sorter, processing incoming messages and placing them in the right mailboxes. It applies filters, sorts spam, and makes sure each email lands exactly where it should.
Here’s how a typical email flows through your system:
- You write an email in your MUA
- The MTA picks it up and finds the best route
- The recipient’s MDA processes and delivers it
- Their MUA displays the message
Understanding these components helps you build a more reliable mail server. Each part can be fine-tuned to match your needs, whether you’re running a small business server or managing email for a larger organization.
Setting Up Linux Mail Server
Time to roll up your sleeves – this is where your mail server starts taking shape. Installing a Linux Postfix mail server gives you a rock-solid foundation for email delivery.
Step 1: Install Postfix
Open your terminal and run:
sudo apt update && sudo apt install postfixDuring installation, select “Internet Site” when prompted. This tells Postfix your default mail server will handle emails for domains you own.
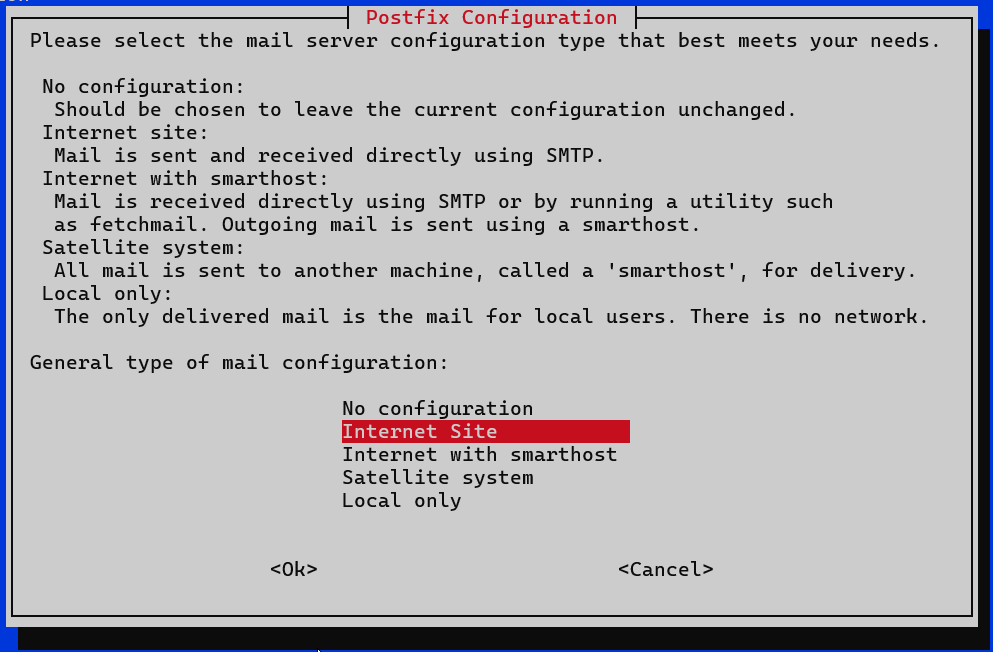
Step 2: Configure Core Settings
Edit /etc/postfix/main.cf to set your server’s identity:
myhostname = mail.yourdomain.com
mydomain = yourdomain.com
mydestination = $myhostname, localhost.$mydomain, $mydomain- myhostname: Your server’s full domain (like the return address on an envelope).
- mydomain: The domain you’re managing emails for.
- mydestination: Lists domains this server will accept emails for.
Step 3: Lock Down Access
Restrict which networks can relay emails through your server. Add this to main.cf:
mynetworks = 127.0.0.0/8 [::1]/128 This limits email sending to localhost initially – you’ll expand this later once authentication is set up.
Step 4: Test the Setup
Check if Postfix is running:
systemctl status postfixIf it’s running, it should look like this:
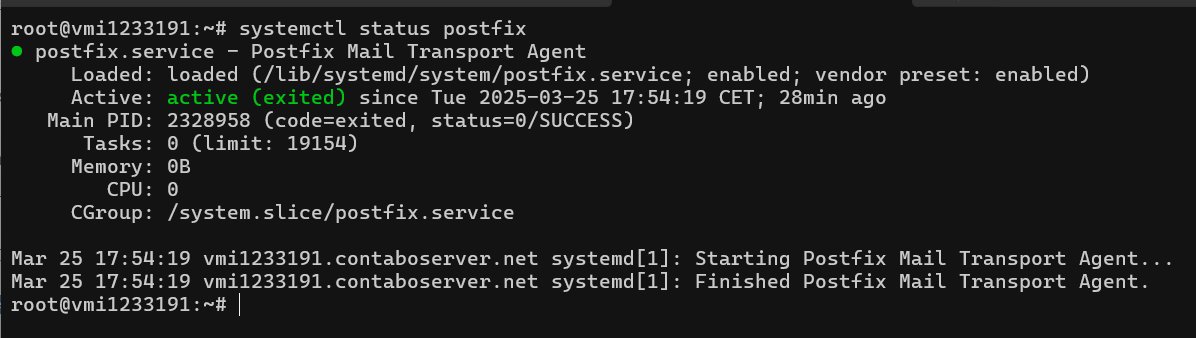
If it is not, start it:
systemctl start postfix Once it’s active, test SMTP connectivity:
telnet localhost 25You should see a response like 220 mail.yourdomain.com ESMTP Postfix. Type quit to exit.
Why Start with Postfix?
Postfix acts like a well-organized mailroom:
- Receiving: Accepts emails from users or other servers.
- Processing: Applies filters, checks for spam.
- Routing: Determines the fastest path to the recipient’s server.
Pairing Postfix with a VPS from Contabo ensures each step happens at lightning speed, thanks to NVMe storage reducing I/O bottlenecks.
Troubleshooting Tips
Emails stuck in queue? Run postqueue -p to view pending messages.
Configuration errors? Check logs with tail -f /var/log/mail.log.
By now, your server can send and receive emails locally. In the next section, we’ll unlock its full potential by fine-tuning security and performance settings.
Configure Linux Mail Server
Now that Postfix is installed, let’s fine-tune your Postfix configuration in Linux it to handle your email traffic securely and efficiently. Think of this step as adjusting the settings on a high-performance engine – every parameter matters for optimal operation.
Core Configuration Parameters
Open /etc/postfix/main.cf in your preferred text editor. Here are the key settings to optimize:
myhostname = mail.yourdomain.com
mydomain = yourdomain.com
myorigin = $mydomain
mydestination = $myhostname, localhost.$mydomain, $mydomain
mynetworks = 127.0.0.0/8 [::1]/128
inet_protocols = all
mail_spool_directory = /var/spool/mail
myhostname: Your server’s full domain name. This acts like a return address on every email sent.mydomain: The primary domain your server manages.myorigin: Defines the domain appended to unqualified email addresses (e.g., “user” becomes “[email protected]“).mydestination: Lists domains your server accepts emails for. Keep this tight to prevent unintended relay.mynetworks: Restricts which IPs can send emails without authentication. Start with localhost only for security.inet_protocols: Set to “all” to support both IPv4 and IPv6 connections.mail_spool_directory: Defines where incoming mail is stored. By default, mail is delivered to /var/spool/mail with a separate file for each user. If you add a trailing slash (mail_spool_directory = /var/spool/mail/), Postfix will use the Maildir format instead of the traditional mbox format.
Security First
Limit exposure by adjusting the SMTP banner – this header reveals software versions to potential attackers. Add this to main.cf:
smtp_banner = $myhostname ESMTP Now your server won’t broadcast that it’s running Postfix, making it harder to exploit known vulnerabilities.
Storage Optimization
By default, Postfix stores emails in /var/spool/postfix. If you’re using a VPS from Contabo with NVMe storage, you’ll benefit from faster read/write speeds when handling large email volumes. For high-traffic setups, consider mounting a separate NVMe partition:
queue_directory = /mnt/nvme/postfix Test Your Configuration
After saving changes, reload Postfix:
sudo systemctl reload postfix Check for errors:
tail -f /var/log/mail.log Look for lines containing “reloading” or “fatal” to catch issues early.
Why Configuration Matters
Properly tuned settings:
- Prevent your server from being hijacked for spam
- Ensure emails reach their destinations without delays
- Reduce resource usage through efficient queuing
Next up: Learn how to monitor your mail queue and troubleshoot delivery hiccups before they impact users.
Checking Mail Queue
Even the best mail servers occasionally hit snags. When emails pile up undelivered, your Postfix mail queue acts like a digital waiting room – messages sit patiently until they can proceed. Here’s how to keep this process running smoothly.
Monitor Active Queues
Use Postfix’s built-in tool to check the Linux mail queue:
postqueue -pThis lists every email in the check mail queue, showing:
- Sender/Recipient: Who’s waiting to deliver/receive
- Queue ID: Unique identifier for tracking
- Deferral Reason: Why delivery stalled (network issues, DNS errors, etc.)
Troubleshoot Stuck Emails
Spot a message stuck in “deferred” status? Investigate with:
postcat -q [Queue_ID] This reveals the email’s full headers and error details. Common fixes include:
- Updating DNS records if recipient domains changed
- Adjusting
mydestinationif accepting mail for unconfigured domains - Increasing timeout limits for slow remote servers
Clear the Queue Safely
To remove all deferred emails:
postsuper -d ALL deferred Caution: This deletes undelivered messages! Only use it after backing up critical emails.
Next, we’ll test your server’s end-to-end functionality to ensure everything works as intended.
Test Mail Server
Your mail server is up and running – but does it actually deliver emails? Let’s validate your setup with a real-world mail server test that ensures messages flow smoothly from sender to recipient.
Step 1: Verify DNS Records
First, check MX records (Mail Exchange) to ensure that they point to the correct server. Open a terminal and run:
dig MX yourdomain.com +short You should see output like:
10 mail.yourdomain.com If not, update your DNS settings to point to your server’s IP. This tells other mail servers where to deliver emails for your domain.
Step 2: Send a Test Email
Use the mail command to send an email from your server:
echo "check mail server" | mail -s "Server Test" [email protected] Replace [email protected] with an external email you control (Gmail, Outlook, etc.).
Step 3: Check Delivery
If the email doesn’t arrive within 5 minutes:
- Inspect the mail queue:
postqueue -p - Review logs for errors:
grep 'status=sent' /var/log/mail.logTroubleshooting Pro Tip
Test locally first! Send an email between two users on your server:
echo "Local test" | mail -s "Internal Test" [email protected] Check delivery with:
sudo tail -f /var/mail/user Next, we’ll lock down your server with essential security measures to keep spammers and hackers at bay.
Secure Linux Mail Server
Your mail server is now operational, but leaving it unsecured is like leaving your front door wide open in a busy neighborhood. Let’s fortify your email server security against spammers, hackers, and data leaks.
SMTP User Authentication
Enable SMTP authentication to act like a bouncer for your secure mail server – it verifies users before letting them send messages. Without it, attackers could hijack your server to spam others.
Enable SASL Authentication:
sudo apt install libsasl2-modules sasl2-bin Edit /etc/postfix/main.cf:
smtpd_sasl_auth_enable = yes
smtpd_sasl_type = dovecot
smtpd_sasl_path = private/auth This ties Postfix to Dovecot for authentication.
SSL/TLS Encryption
Enable mail encryption to ensure no one can snoop on messages in transit. Let’s use Let’s Encrypt for free certificates:
Generate Certificates:
sudo certbot certonly --standalone -d mail.yourdomain.com Configure Postfix:
smtpd_tls_cert_file=/etc/letsencrypt/live/mail.yourdomain.com/fullchain.pem
smtpd_tls_key_file=/etc/letsencrypt/live/mail.yourdomain.com/privkey.pem
smtpd_use_tls=yes Why TLS Matters:
- Encrypts emails between servers (like sealing an envelope)
- Boosts deliverability (Gmail/Yahoo now require TLS)
Configure Mail Relay
Limit relay to trusted domains/IPs to prevent abuse:
relay_domains = yourdomain.com, example.net
smtpd_relay_restrictions = permit_mynetworks, reject_unauth_destination Now only emails for yourdomain.com or example.net will be relayed.
SPF: Sender Policy Framework
An SPF record tells other servers which IPs can send emails for your domain – like a guest list for your mail server.
Add DNS Record:
v=spf1 mx -all SPF security authorizes your MX servers and blocks others.
DKIM: DomainKeys Identified Mail
DKIM security adds a digital signature to outgoing emails, proving they’re legit.
Install OpenDKIM:
sudo apt install opendkim opendkim-tools Generate Key:
opendkim-genkey -s default -d yourdomain.com Add the public key to your DNS as a TXT DKIM record.
DMARC: Domain-based Message Authentication
A DMARC record tells receiving servers how to handle emails that fail SPF/DKIM checks.
Sample DNS Record:
v=DMARC1; p=quarantine; rua=mailto:[email protected]DMARC security quarantines suspicious emails and sends reports to you.
Next Up: Learn to combat spam with SpamAssassin – turn your server into a spam-filtering powerhouse.
Eliminate Spam with SpamAssassin
Spam emails are like uninvited guests – they clutter your inbox and waste resources. SpamAssassin acts as your digital bouncer, using smart filters to keep junk mail out while letting legitimate messages through.
Step 1: Install SpamAssassin
Run these commands to install the spam fighter and its client:
sudo apt update && sudo apt install spamassassin spamc Create a dedicated user for the service:
sudo adduser spamd --disabled-login Step 2: Configure Filter Rules
Customize your SpamAssassin configuration by editing /etc/spamassassin/local.cf to set your filtering preferences. Suggested best SpamAssassin settings are below:
required_score 5.0
use_bayes 1
bayes_auto_learn 1
header RBL_CHECK eval:check_rbl('zen.spamhaus.org')required_score: Emails scoring 5+ get flagged (adjust to your tolerance).bayes_auto_learn: Enables adaptive learning—SpamAssassin improves as it processes more emails.RBL_CHECK: Blocks emails from servers on Spamhaus’s realtime blackhole list.
Step 3: Integrate with Postfix
Modify /etc/postfix/master.cf to route emails through SpamAssassin:
smtp inet n - - - - smtpd
-o content_filter=spamassassin
spamassassin unix - n n - - pipe
user=spamd argv=/usr/bin/spamc -f -e /usr/sbin/sendmail -oi -f ${sender} ${recipient}Reload both services:
sudo systemctl restart postfix spamassassinHow It Works
SpamAssassin scores emails using:
- Header Analysis: Checks for suspicious patterns (e.g., mismatched sender domains).
- Content Scanning: Flags phrases like “urgent investment opportunity.”
- Blocklist Lookups: Blocks servers with poor reputations.
- Bayesian Filtering: Learns from your inbox to refine detection over time.
Testing Your Setup
Send a test email from an external account. Let SpamAssassin check headers for spam markers:
grep 'X-Spam-Status' /var/log/mail.logIf you see Yes or a high score, SpamAssassin is working.
Optimizing for Performance
Servers from Contabo with NVMe storage handle SpamAssassin’s intensive I/O tasks efficiently. For high-traffic setups, mount a separate NVMe partition for SpamAssassin’s temporary files:
bayes_path = /mnt/nvme/spamassassin/bayesNext, we’ll set up POP3/IMAP access so users can retrieve emails securely.
POP3 and IMAP Basics
Now that your server is filtering spam, how do users actually access their emails? Enter POP3 and IMAP – two protocols that handle email retrieval but work in fundamentally different ways. Choosing between them affects everything from storage to multi-device access.
IMAP vs. POP3: The Protocol Showdown
- POP3 protocol (Post Office Protocol 3): Downloads emails to a device and typically deletes them from the server. Think of it as grabbing physical mail from your mailbox – once you take it out, it’s no longer there for others to see.
- IMAP protocol (Internet Message Access Protocol): Syncs emails across devices by keeping them on the server. Imagine a shared bulletin board where everyone sees the same updates in real time.
Ports and Security
Both protocols support encrypted and unencrypted connections:
- POP3 ports:
- Unencrypted: Port 110
- Encrypted (SSL/TLS): Port 995
- IMAP ports:
- Unencrypted: Port 143
- Encrypted (SSL/TLS): Port 993
Always use encrypted ports to protect login credentials and email content.
When to Choose Which
- Use POP3 If:
- You check email from one device
- You want to conserve server storage
- Internet access is spotty (emails work offline)
- Use IMAP If:
- You access email from multiple devices (phone, laptop, tablet)
- Your team shares a mailbox
- You need server-side search/organization
Up next: We’ll configure Dovecot to handle POP3/IMAP securely, ensuring your users retrieve emails without compromising safety.
Dovecot on Linux
What is Dovecot? Think of it as your mailroom clerk – it organizes incoming emails into proper folders and ensures users can retrieve them securely via POP3 or IMAP. This lightweight yet powerful MDA (Mail Delivery Agent) works seamlessly with Postfix to create a complete Dovecot mail server.
Install Dovecot
Get started with a single command:
sudo apt install dovecot-imapd dovecot-pop3d This installs both IMAP and POP3 support. Check if it’s running:
systemctl status dovecot You’ll see “active (running)” if everything’s working.
Configure Dovecot
Modern email users expect their messages to sync across devices. Configure Maildir storage in /etc/dovecot/conf.d/10-mail.conf:
mail_location = maildir:~/Maildir This stores emails in a structured directory format, ideal for IMAP’s multi-device sync.
Next, link Dovecot Linux to your Let’s Encrypt certificates in /etc/dovecot/conf.d/10-ssl.conf
ssl_cert = </etc/letsencrypt/live/mail.yourdomain.com/fullchain.pem
ssl_key = </etc/letsencrypt/live/mail.yourdomain.com/privkey.pem Secure Dovecot
Force encrypted connections to protect login credentials:
ssl = required
ssl_min_protocol = TLSv1.2 Disable outdated protocols like SSLv3 in /etc/dovecot/conf.d/10-ssl.conf.
Test Your Setup
- Send a test email to
[email protected]. - Configure Thunderbird or Outlook to connect via IMAP:
- Server:
mail.yourdomain.com - Port:
993(IMAPS) or995(POP3S) - Encryption: SSL/TLS
- Server:
If emails aren’t appearing, check Dovecot’s logs:
tail -f /var/log/mail.log | grep dovecotNext, we’ll explore how control panels like Plesk simplify email management – perfect for teams wanting GUI convenience.
Mail Server Using Web Hosting Control Panel
Not everyone wants to configure mail servers through the command line – and that’s okay! Web control panels like Plesk and cPanel offer intuitive interfaces to manage email settings while handling the backend complexity for you.
Plesk Mail Server
Plesk acts like a dashboard for your mail server, turning intricate configurations into simple clicks. With Plesk servers from Contabo, you get:
- One-Click Email Setup: Create accounts, aliases, and forwarding rules instantly.
- Automated Security: Built-in tools configure SPF, DKIM, and TLS certificates.
- Domain Management: Handle multiple domains from a single interface.
Need to set up a mailing list or autoresponder? Plesk’s extensions add these features without touching a config file.
cPanel Mail Server
cPanel works like a traffic controller for your emails, streamlining delivery and retrieval. On cPanel servers from Contabo, you’ll find:
- Automated DNS Management: MX records update automatically when adding domains.
- Spam Filter Centralization: Adjust SpamAssassin rules through a graphical interface.
- Resource Monitoring: Track storage and bandwidth usage in real time.
Setting up a catch-all email or configuring vacation responders takes seconds. Plus, cPanel’s documentation and community support make troubleshooting accessible even for newcomers.
Mail Server with Contabo
Running your own Linux mail server gives you complete control over data security and customization. Let’s explore how to use Contabo servers to build a secure, high-performance mail server tailored to your needs.
Why Build on Contabo?
Contabo servers give you enterprise-grade hardware at budget-friendly prices. Whether you choose a VPS, VDS, or Dedicated Server, you’ll get:
- NVMe Storage: fast NVMe drives (or SSD alternatives) ensure quick access to email databases.
- Plenty of RAM: handles concurrent IMAP/POP3 connections smoothly.
- Unmetered Incoming Traffic: Receive unlimited emails without worrying about bandwidth caps.
- Global Data Centers: Deploy closer to your users for reduced latency.
Key Features for Email Hosting
- DDoS Protection: Always-on safeguards keep your server online during attacks.
- GDPR Compliance: Host emails in German/EU data centers to meet strict privacy regulations.
- Scalability: Upgrade CPU cores (4–20 vCPUs with VPS) and storage as your user base grows.
- Snapshots: Safeguard configurations with backups (depending on plan).
Getting Started
- Choose a Server:
- From cost-effective VPS to larger setups, we’ve got you covered.
- Set Up Software:
- Install Postfix/Dovecot via command line (as outlined earlier).
- Configure SSL/TLS using Let’s Encrypt for encryption.
- Monitor Performance:
Use tools likehtopandmail.logto track resource usage and delivery success rates.
Conclusion
Setting up your own Linux mail server might feel daunting at first, but as you’ve seen, it’s entirely achievable with the right tools and guidance. You’ve learned how to configure Postfix for email routing, secure connections with Let’s Encrypt, and combat spam using SpamAssassin. You’ve explored protocols like IMAP and POP3, integrated Dovecot for seamless mail retrieval, and even tested your server’s performance end-to-end.
The real power lies in pairing this knowledge with infrastructure that keeps up. Contabo servers offer the NVMe speed, scalability, and reliability needed to run a high-performance mail server without breaking the bank.
Ready to put this into practice? Your email, your rules. Let’s get sending.
