
In a previous article, we discussed some free tools to help you monitor and test the security of your server or VPS (Virtual Private Server). In this article, we will take a closer look at Indicators of a compromised Instance and provide practical steps on how to effectively respond. These measures are essential for protecting your digital assets and sensitive information in an increasingly risky online environment. So, let us dive in and explore the essentials to safeguard your digital world.
Common Indicators of Instance Compromise
This chapter explores practical indicators that can act as early warnings of compromise, helping you protect your digital assets. We’ll dig into specific signs like odd system behavior, performance issues, unusual log entries, unexpected network patterns, and unauthorized access attempts. By understanding and identifying these signs, you’ll be better equipped to strengthen your defenses and respond effectively to security threats.
1. Unusual System Behavior and Performance Degradation
One of the first signs of a compromised system is often unusual behavior and a noticeable drop in performance. This can manifest as slow response times, unexpected crashes, or unusual system resource utilization. Here is an example of how you can monitor system performance using the `top` command in a Linux-based system:
topThe `top` command displays real-time information about system processes and resource usage. Look for any processes consuming excessive CPU or memory resources that you cannot explain.
In Windows, a similar tool would be the Windows Task Manager. To open it either search for “Task Manager” in the Windows search bar or press [CTRL] + [SHIFT] + [ESC] to access it.
It looks like this:
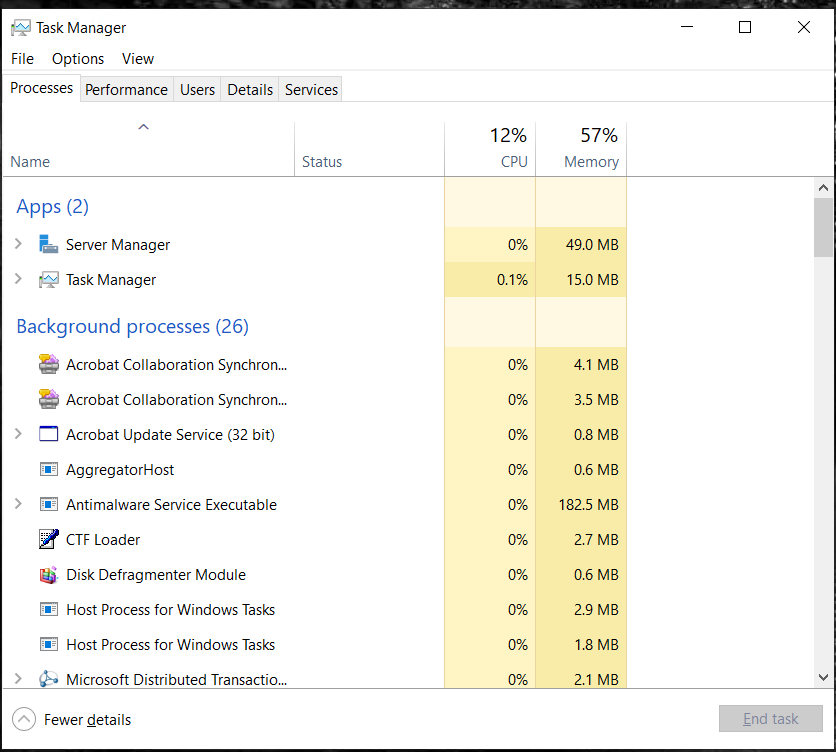
Here you can see all processes that are running – active and background ones – and the amount of resources they are using. Look out for unknown processes that use a lot of system resources. This could be an indicator that something sketchy is going on.
2. Suspicious Log Entries and Anomalies
Linux:
Monitoring system logs can also help detect suspicious activities. Attackers may attempt to cover their tracks, but unusual log entries can reveal their presence. You can check the system logs in a Linux system using the `tail` command. This command will show you the last 10 entries in that file:
tail -f /var/log/syslogLook for any unfamiliar entries or repeated login failures that could indicate a brute-force attack or unauthorized access.
Windows:
Windows Server includes a special tool called “Event Viewer” where relevant system logs are saved.
To access the Event Viewer press [Win] +[X] and select “Event Viewer” from the menu.
In the Event Viewer window, expand “Windows Logs” on the left sidebar.
You will find several log categories, including “Security,” “Application,” and “System.” Click on the appropriate log category based on what you want to investigate.
Now, let us focus on the “Security” log:
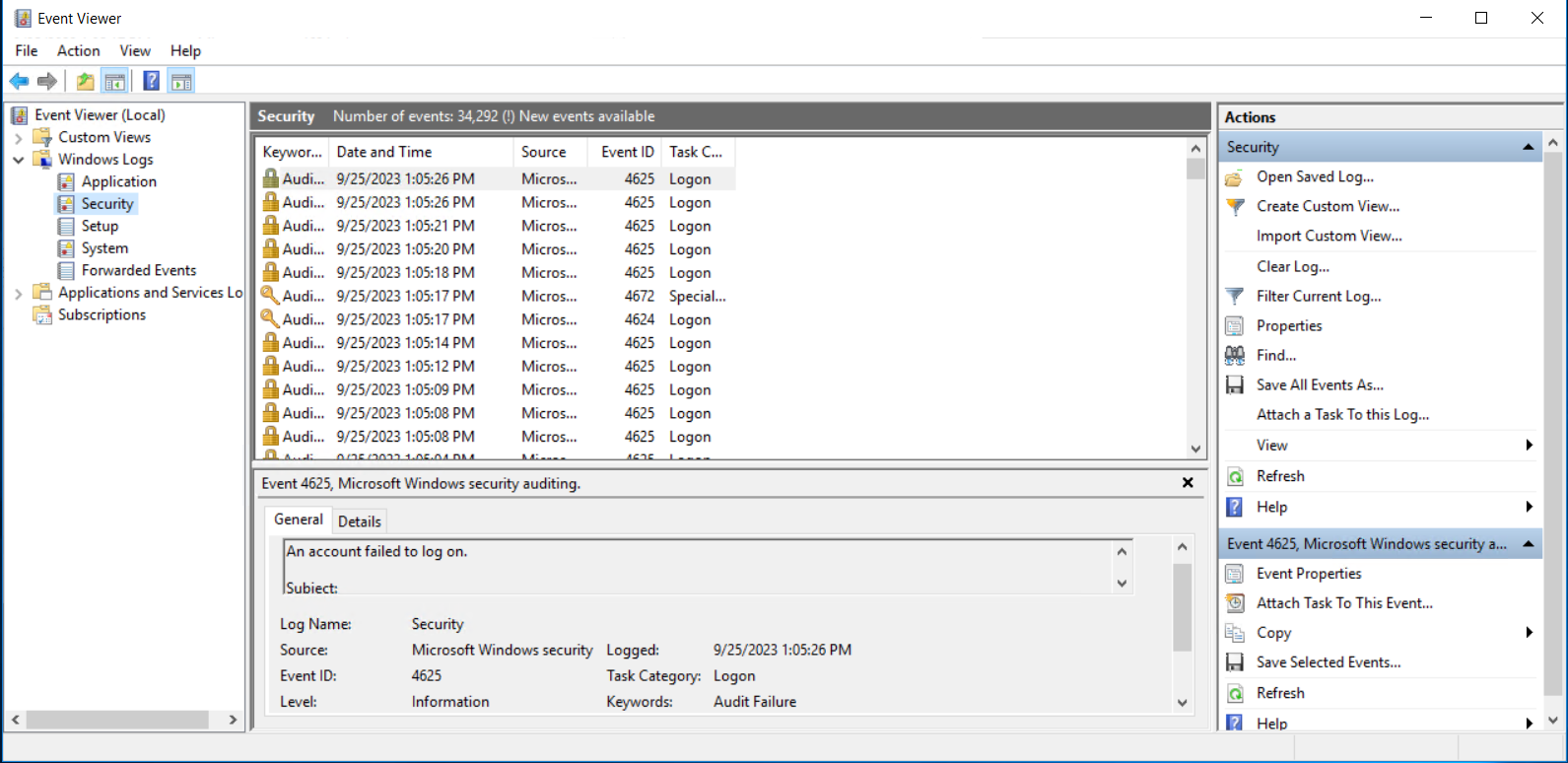
In the “Security” log, you can look for any unfamiliar or suspicious entries. Pay particular attention to repeated login failures, which could indicate brute-force attacks or unauthorized access attempts.
3. Unauthorized Access Attempts and Login Failures
Another clear sign of your instance being compromised is unauthorized access attempts and login failures. You can review authentication logs on a Linux system using the `auth.log` file:
cat /var/log/auth.logKeep an eye out for repeated login failures or successful logins from unfamiliar IP addresses or user accounts.
These are just a few common indicators of compromise to be aware of. Monitoring your system regularly and staying vigilant for these signs is a basic task for maintaining the security of your digital environment.
Early Warning Signs
When it comes to identifying an already compromised system, it is not just the obvious signs of compromise that matter; it is also the subtle ones that can provide early warnings of a potential breach. In this chapter, we’ll take a look at the significance of identifying these early warning signs, the importance of continuous monitoring, and red flags to look for in system logs and user activities.
Identifying Subtle Signs of Instance Compromise
While unusual system behavior and performance degradation are often obvious signs of compromise, sophisticated attackers may leave behind more discreet traces. These subtle signs can include:
- Subtle Changes: Small, unexplainable changes in system configurations, files, or permissions.
- Unusual Outbound Traffic: Slight increases in outbound network traffic, which could indicate data exfiltration (theft).
- Phishing Attempts: Subtle phishing attempts, such as suspicious emails or URLs that may not be immediately obvious.
- Slow and Steady Attacks: Attackers employ “low and slow” techniques to avoid detection, making their activities less noticeable.
Red Flags in System Logs and User Activities
System logs and user activities provide valuable insights into the health and security of your environment. Red flags to watch for in these areas include:
- Privilege Escalation: Unusual requests or actions by users attempting to gain unauthorized access or escalate their privileges.
- Suspicious Processes: Processes running with elevated privileges or attempting to access sensitive data.
- Unusual Account Activity: Accounts being created, modified, or accessed outside of regular hours.
Utilize log analysis tools and security information and event management (SIEM) solutions to help sift through vast amounts of data and identify these red flags efficiently.
Detecting Data Breaches
Data breaches can have devastating consequences, ranging from reputational damage to financial losses and legal ramifications. Detecting data breaches early is crucial to minimize their impact. In this chapter, we will explore methods for recognizing signs of data exfiltration, monitoring unauthorized access to sensitive data, and the role of anomaly detection in data breach detection.
Recognizing Signs of Data Exfiltration
Data exfiltration is the unauthorized transfer of data from your network to an external location controlled by cybercriminals. To identify signs of data exfiltration, look for:
- Unusual Outbound Traffic: Monitor network traffic for unexplained spikes in outbound data, especially to unfamiliar IP addresses, unusual ports, or to newly registered or autogenerated domains that end with “.xyz” or similar.
- Large File Transfers: Keep an eye on file transfer activity, particularly if it involves sensitive data, and be vigilant for unusually large or frequent transfers. But keep in mind that attackers might take a slow approach when it comes to exfiltrating your data. It may take weeks or even months until they finished.
- Data Encryption: Attackers may encrypt exfiltrated data to avoid detection, so monitor for unexpected encryption processes.
Implementing data loss prevention (DLP) solutions and network traffic analysis tools can help you recognize and mitigate data exfiltration attempts.
Monitoring for Unauthorized Access to Sensitive Data
Unauthorized access to sensitive data is a common precursor to data breaches. Here are some ideas on how to monitor such things:
- Access Control and Permission Audits: Regularly review access controls and permissions for sensitive data to ensure that only authorized users have access.
- User Behavior Analytics (UBA): Implement UBA solutions that analyze user activities and detect unusual behavior patterns, such as unauthorized access or data copying.
- File Integrity Monitoring (FIM): Use FIM tools to monitor key configuration files, flagging any unauthorized alterations.
The Role of Anomaly Detection in Data Breach Detection
Anomaly detection plays a pivotal role in identifying data breaches. It involves establishing a baseline of normal system behavior and then flagging deviations from that baseline. Key areas for anomaly detection include:
- User Behavior: Identify unusual login times, locations, and patterns of access.
- Network Traffic: Detect anomalies in traffic volume, protocols, and patterns.
- Application Behavior: Monitor for deviations in application usage, such as unusual API calls or database queries.
- File Activity: Identify unexpected changes in files, directories, or file access patterns.
Recognizing External Threats
Your instance is always vulnerable to external threats from potential attackers. We’ll take a look on how to spot signs of these external threats, ways to monitor and block malicious IP addresses and domains, and strategies for dealing with denial-of-service (DoS) attacks.
Signs of External Attackers Targeting Your Instance
It is important to be on the lookout for signs that external attackers might be targeting your instance. Some common signs include:
- Port Scanning: Frequent and sequential connection attempts on various ports, which could be a sign of attackers looking for vulnerabilities.
- Suspicious Login Activity: Multiple failed login attempts, especially from different IP addresses or regions.
- Unusual Traffic Patterns: A sudden increase in traffic or unusual patterns, such as a flood of requests to a specific service.
Monitoring for Malicious IP Addresses and Domains
To protect your instance, it is important to keep an eye out for malicious IP addresses and domains. You can do this by:
- Using Blocklists: Employing reputable IP and domain blocklist to filter out traffic from known malicious sources.
- Utilizing Intrusion Detection Systems (IDS): Implementing IDS solutions to identify and block traffic from IPs exhibiting malicious behavior.
- DNS Filtering: Making use of DNS filtering services to prevent access to malicious domains.
Identifying and Responding to Denial-of-Service (DoS) Attacks
DoS attacks can disrupt your instance by overwhelming it with a flood of traffic. Contabo’s In-Built DDoS Protection can help you deal with these attacks effectively.
Common DoS Attacks 1
Here are the main types of DoS attacks:
| DoS Attack Type | Explanation |
| Ping Flood | Sending an overwhelming number of ICMP Echo Request (ping) packets to a target, causing network congestion and potentially making the target unresponsive. |
| SYN Flood | Exploiting the TCP three-way handshake process by sending a flood of SYN requests to a target, overwhelming its resources, and preventing legitimate connections. |
| UDP Flood | Flooding a target with a high volume of UDP packets, often with spoofed source IP addresses, to consume its bandwidth and resources. |
| HTTP Flood | Overloading a web server by sending an excessive number of HTTP requests, making it unable to serve genuine users. |
| ICMP Flood | Flooding a target with ICMP Echo Request (ping) packets, like Ping Flood, causes network congestion. |
| DNS Amplification | Abusing open DNS resolvers by sending small DNS queries with a spoofed source IP, causing the resolver to send larger responses to the victim, amplifying the attack. |
Common DoS Attacks 2
| NTP Amplification | Utilizing vulnerable Network Time Protocol (NTP) servers to amplify traffic towards a target, creating a DoS situation. |
| Smurf Attack | Broadcasting ICMP Echo Request packets to a network, causing numerous responses to flood the victim’s network. |
| Slowloris | Keeping multiple HTTP connections to a web server open by sending partial HTTP requests, tying up server resources. |
| Teardrop Attack | Sending malformed IP packets with overlapping fragments to crash the target’s operating system or network stack. |
| Application Layer | Targeting application vulnerabilities, such as SQL Injection or Buffer Overflow, to disrupt services or crash the application. |
| Ping of Death | Sending an oversized ICMP Echo Request packet, exceeding the maximum allowed packet size, causing buffer overflows and potential system crashes. |
| DNS Flood | Flooding a DNS server with a high volume of DNS queries, potentially causing it to become unresponsive. |
| HTTP POST Flood | Overloading a web server with a large number of HTTP POST requests, consuming server resources. |
Now let us talk about how to identify and respond to DoS attacks:
- Watch for Traffic Spikes: Keep an eye out for sudden, massive increases in incoming traffic, which might be a sign of a DoS attack.
– Leverage Built-In DDoS Protection: Take advantage of Contabo’s In-Built DDoS Protection by ordering any server at Contabo. Our system can automatically detect and mitigate DoS attacks, ensuring your instance remains accessible.
Incident Response Plan
In an increasingly interconnected digital world, having a robust incident response plan (IRP) is not a luxury but a necessity. Now we will look at the process of developing an incident response plan, underscore the significance of a well-defined incident response team, and outline the essential steps to take when an indicator of compromise is detected.
Developing an Incident Response Plan (IRP)
An incident response plan (IRP) is a comprehensive strategy outlining the actions your organization will take when a security incident occurs. Developing an effective IRP involves the following key steps:
- Risk Assessment: Identify the potential threats and vulnerabilities that your organization faces.
- Team Formation: Assemble a dedicated incident response team with clear roles and responsibilities.
- Plan Creation: Develop a detailed plan outlining the procedures to follow when a security incident occurs.
- Testing and Training: Regularly test the plan through simulated incidents and ensure that your team is adequately trained.
- Documentation: Keep detailed records of incidents, responses, and lessons learned to refine the IRP over time.
- Communication: Establish communication protocols to keep stakeholders informed during an incident.
Steps to Take When an Indicator of Compromise is Detected
When an indicator of compromise (IoC) is detected, swift and decisive actions must be applied. Here are the key steps to follow:
- Isolation: Immediately isolate the affected systems or networks to prevent the incident from spreading.
- Analysis: Investigate the IoC (indicators of compromise) to understand the nature and scope of the incident.
- Containment: Develop a strategy to contain the incident and prevent further damage.
- Eradication: Remove the threat from affected systems and ensure that vulnerabilities are patched.
- Recovery: Restore affected systems and services to normal operations.
- Lessons Learned: Conduct a post-incident analysis to identify areas for improvement in your IRP and overall security posture.
In the next chapter, we will talk about containment strategies in detail.
Containment and Mitigation
This chapter explores the critical steps of isolating the compromised instance, disabling compromised accounts and access points, and removing malicious software and files to minimize damage and restore normality.
Isolating the Compromised Instance
Isolating the compromised instance is the first and most important step in containing the incident. Isolation prevents the incident from spreading further within your network and limits its impact on other systems. Here are some ideas on how to do that:
- Network Segmentation: Use network segmentation to separate the compromised instance from the rest of your network, ensuring that it cannot communicate with other systems.
- Isolation Protocols: Disconnect the compromised instance from the network entirely, physically or through network configurations.
Disabling Compromised Accounts and Access Points
To prevent further unauthorized access and actions, you must disable compromised accounts and access points. This involves:
- Account Lockout: Disable user accounts that have been compromised or are suspected of unauthorized access.
- Password Resets: Initiate password resets for affected accounts to ensure that they cannot be used maliciously.
- Access Point Closure: Close any access points, such as backdoors, that attackers may have used to gain entry.
Removing Malicious Software and Files
Once you have isolated the compromised instance and disabled affected accounts, the next step is to remove malicious software and files. This process includes:
- Antivirus Scans: Run thorough antivirus and anti-malware scans on the compromised instance to identify and remove malicious software.
- File Cleanup: Manually review and delete suspicious or malicious files from the system.
- Patch and Update: Ensure that the compromised instance and any affected software or systems are patched and up to date to eliminate vulnerabilities that may have been exploited.
Regular Backups are key to not losing important data in case of a compromised instance. Therefore, it is good to have proper backup strategies.
Investigation and Analysis
Conducting a thorough investigation and analysis of the security incident is part of preventing such incidents from repeating. Here are some steps to conduct a post-incident analysis, gather evidence and logs for forensic analysis, and identify the root cause of the compromise.
Conducting a Thorough Post-Incident Analysis
After containing the incident and mitigating immediate threats, the next step is to conduct a comprehensive post-incident analysis. This helps you understand the full scope of the incident, its impact, and learn lessons for future prevention. Key steps in the analysis include:
- Document Everything: Maintain detailed records of the incident, including when it was detected, how it was contained, and the actions taken during the response.
- Interviews: Interview involved parties, including your incident response team, affected users, and IT personnel, to gather insights and perspectives on the incident.
- Timeline Reconstruction: Create a timeline of the incident, detailing each step from the initial compromise to the incident’s containment.
- Identify Affected Assets: Determine which systems, data, and resources were compromised, potentially exfiltrated, or otherwise affected.
Gathering Evidence and Logs for Forensic Analysis
To understand the extent of the incident and gather evidence for potential legal and regulatory requirements, you will need to gather and preserve relevant logs and evidence. This process involves:
- Log Collection: Retrieve and secure logs from affected systems, network devices, and any other relevant sources.
- Network Traffic Capture: If applicable, capture network traffic during the incident for later analysis.
Identifying the Root Cause of the Instance Compromise
Determining the root cause of the compromise is a fundamental aspect of post-incident analysis. To identify the root cause, follow these steps:
- Vulnerability Assessment: Evaluate the system and network for vulnerabilities that may have been exploited by the attacker.
- Incident Reconstruction: Use the timeline and evidence to reconstruct the incident and identify how the attacker gained access and moved within your environment.
Prevention and Hardening
Preventing future security incidents and fortifying your instance’s security posture is an ongoing process. In this chapter, we will explore strategies for strengthening your instance’s security, implementing best practices for future protection, and the importance of continuous security monitoring and improvement. To prevent future compromises and harden the security of your server read our in-depth guides “The Importance of Patching and Patching Best Practices (Linux & Windows)” and “Free Tools to Monitor & Test the Security of Your Server or VPS” for additional insights.
Strengthening Your Instance’s Security Posture
Strengthening your instance’s security posture is a proactive approach to reducing vulnerabilities and deterring potential threats. Key strategies include:
- Access Control: Review and fine-tune user access and permissions to ensure the principle of least privilege.
- Regular Updates: Keep your system and software up to date with security patches to address known vulnerabilities.
- Firewalls and Intrusion Detection: Implement firewalls and intrusion detection systems to filter network traffic and detect suspicious activities.
- Secure Configuration: Ensure that your systems are securely configured based on best practices and industry standards.
- Security Awareness Training: Train your users and staff in security best practices to mitigate human error.
Implementing Best Practices for Future Protection
Implementing best practices for future protection is the way to go for maintaining a strong security posture. This includes:
- Regular Patching: Establish a patch management process to ensure timely application of security updates.
- Testing: Test patches in a controlled environment before deploying them to production systems.
- Prioritization: Prioritize patching based on the severity of vulnerabilities and the criticality of affected systems.
- Vendor Notifications: Stay informed about security updates from software vendors and apply them promptly.
- Backup and Recovery: Maintain regular backups of critical data to facilitate recovery in case of a security incident.
Continuous Security Monitoring and Improvement
Security maintenance is an ongoing process and includes continuous monitoring and improvement. These steps can help you monitor the security of your server:
- Vulnerability Scanning: Regularly scan your systems and networks for vulnerabilities.
- Log Analysis: Analyze logs for signs of unusual behavior or potential security incidents.
- Intrusion Detection: Employ intrusion detection systems to identify and respond to threats in real-time.
- Security Metrics: Establish key security metrics to measure and improve your security posture over time.
Conclusion
Whether a security incident will occur is not a matter of if, but when. By developing and maintaining a robust incident response plan, assembling a skilled incident response team, and consistently implementing security best practices, you can better protect your digital assets.
Certainly, vigilance and a security-first mindset must be at the forefront of your digital endeavors. Additionally, cyber threats are continually evolving, and attackers are becoming increasingly sophisticated. To address this, staying informed about emerging threats, regularly assessing, and improving your security measures are crucial steps. Moreover, fostering a culture of cybersecurity awareness within your organization can help safeguard your instance and data against the ever-present risks.
Absolutely, cybersecurity is a continuous journey; moreover, there is no one-size-fits-all solution. It demands dedication, adaptability, and a commitment to staying ahead of potential threats.