
Modern internet privacy concerns and the need for secure remote access have made VPN technology essential for individuals and businesses alike. While commercial VPN services offer convenience, they come with limitations: you’re trusting a third party with your data, dealing with potential logging policies, and often experiencing inconsistent performance across shared infrastructure.
This comprehensive guide teaches you to build your own WireGuard VPS solution from scratch. You’ll learn every step needed to deploy a high-performance, self-hosted VPN server that you fully control. Whether you’re securing personal browsing, enabling remote work access, or protecting sensitive communications, this tutorial provides the technical knowledge and practical commands to create a robust, scalable VPN infrastructure. Prefer a simpler setup? Because WireGuard is open-source, you can either follow our manual instructions or use Contabo’s free 1-Click WireGuard option to get a working server in minutes. The rest of this guide explains both paths so you can pick the right one.
Introduction: Why Set Up a WireGuard VPS?
A WireGuard VPS setup is one of the most powerful ways to take control of your online security and network access. Instead of depending on commercial VPN providers, hosting your own WireGuard server on a VPS means you decide where your traffic flows, who manages the connections, and how your data is handled. This self-hosted approach gives you independence, transparency, and the freedom to optimize performance for exactly what you need.
WireGuard represents a next-generation VPN protocol designed for speed and simplicity without compromising security. With a fraction of the code compared to older protocols like OpenVPN or IPSec, it’s less error-prone, easier to audit, and faster in performance. When deployed on a VPS, WireGuard provides secure and high-speed tunnels – whether you’re browsing safely on public Wi-Fi, protecting remote team communications, or securing access to your home network from anywhere in the world.
Prefer the Easy Route? Install WireGuard in 1-Click at Contabo (free)
If you don’t want to follow the manual steps listed in this guide, you can now deploy WireGuard + WGDashboard on a Contabo VPS with a single click and at no extra cost beyond your VPS plan. It’s the fastest way to get a working tunnel and a simple web UI for managing peers.
How to Install WireGuard + WGDashboard?
If you want to set up a new instance with the 1-Click WireGuard Add-On:
- Choose your desired product on the WireGuard on VPS page.
- Select your preferred location and set a password (used for both the VPS and the application).
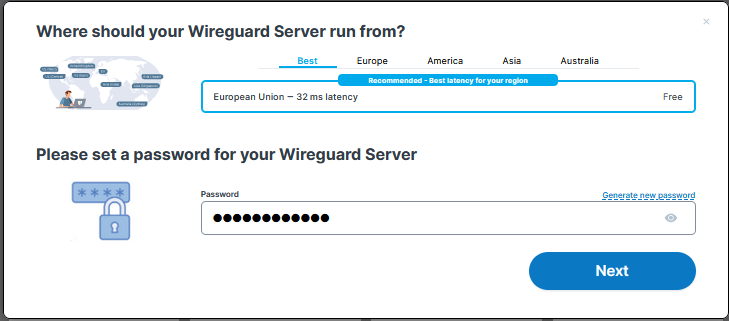
- Complete the order process.
- Log in to the Contabo Customer Control Panel and navigate to ‘VPS‘.
- Please note that it may take up to 30 minutes for your application to be installed and activated. Once it’s installed, you can access the application directly by clicking on its logo under the ‘Quick Action’ section on the right side.
If you are an existing customer and you want to run the application on an existing instance:
- In the VPS section, choose the instance you want your application to be installed on.
- Click on the three vertical dots under ‘More’, then click ‘Reinstall’.
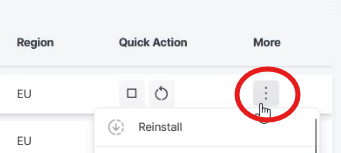
- Select your preferred installation type and configure it.
- Click ‘Install‘.
- The application button will appear under ‘Quick Action’. You can access the application directly by clicking on the icon of the application. Please note that it may take up to 30 minutes for your application to install.
Prerequisites: Choosing a VPS Provider for WireGuard
When considering how to set up WireGuard, the very first step isn’t installation – it’s choosing a reliable VPS provider. WireGuard can run on virtually any Linux distribution, but the performance, security, and flexibility of your VPN depend heavily on the server you select.
At a minimum, look for a VPS that provides:
- 1 CPU core and at least 512 MB RAM (sufficient for a small personal VPN)
- Stable bandwidth, with enough transfer speed for smooth streaming and file sharing
- Full root access, essential for package installation, network configuration, and firewall management
When comparing VPS providers, keep these factors in mind:
- Server location: Choose a VPS data center that’s close to your physical location for speed and reliability, or select one in the region you want to appear in to bypass geo-restrictions. With a VPN, your virtual location can match where you need access most, unlocking global content and local advantages.
- Scalability: If you plan to connect several peers – friends, coworkers, or your own devices – make sure the VPS provider offers straightforward options to upgrade CPU, RAM, and bandwidth as your network grows. Many hosts allow you to scale resources up or down without downtime.
- Security features: Prioritize providers that include extras like DDoS protection, automated backups, and private networking. Power users may also want IPv6 support or the ability to load custom kernel modules for advanced configurations.
So why not just use a commercial VPN instead? With a VPS-based WireGuard setup, you eliminate the trust gap that comes with routing all your internet traffic through someone else’s servers. You know exactly what’s installed, where your data flows, and who has access. Plus, a VPS is versatile: you can run WireGuard alongside self-hosted apps, development tools, or other services.
By picking the right VPS provider from the beginning, you lay the groundwork for a smooth, secure, and scalable WireGuard installation in the next step.
Server Preparation & WireGuard Installation
To install WireGuard properly, start by ensuring your VPS is fully updated and ready to receive new packages. Keeping your system current helps the installation go smoothly and minimizes security vulnerabilities.
Update your server using your distribution’s package manager:
Ubuntu/Debian:
sudo apt update && sudo apt upgrade -y CentOS/Fedora:
sudo dnf update -y Next, it’s wise to synchronize your server’s clock using NTP (Network Time Protocol), since time mismatches can disrupt VPN handshakes.
With preparation done, proceed to installation. WireGuard is included in default repositories for many Linux distributions:
Ubuntu/Debian:
sudo apt install wireguard -y CentOS 8:
sudo dnf install epel-release elrepo-release –y
sudo dnf install kmod-wireguard wireguard-tools Fedora:
sudo dnf install wireguard-tools -y After the installation, verify it with:
wg --version At this point, your step to install a WireGuard server is complete. With the required tools installed, you’re ready to move on to generating cryptographic keys and configuring your WireGuard VPN.
Generating Public and Private Keys
WireGuard key generation is the essential first step for securing your VPN. WireGuard uses a cryptographic pair – a private key (always kept secret) and a public key (shared with peers) – to ensure only authorized devices can connect and exchange encrypted traffic.
One-Liner: Generate Both Keys at Once
To quickly create your server’s keys in your working directory, use:
wg genkey | tee server_private.key | wg pubkey > server_public.key This creates two files in your current directory:
server_private.keyis your secret. Keep it safe.
server_public.keycan be shared with any peer that will connect.
If saving keys to a system directory like /etc/wireguard/, add sudo for permissions:
wg genkey | sudo tee /etc/wireguard/server_private.key | wg pubkey | sudo tee /etc/wireguard/server_public.key Both files are created immediately – no extra commands are needed.
Two-Step Method
If you want to generate the private key first, then the public key later:
- Generate the private key:
wg genkey | tee server_private.key - Generate the public key from the saved private key:
wg pubkey < server_private.key > server_public.key Key Format and Security
Each key will appear as a 44-character base64 string (like VQF1+gjxBdtS...=). Double-check that your output looks like this. Set permissions so only root can read the private key:
sudo chmod 600 /etc/wireguard/server_private.key or
chmod 600 server_private.key Keep the private key confidential and share the public key only with clients you want to connect. The private key will be referenced in your server config; the public key will be handed out as needed to authorized peers.
Configuring the WireGuard Server Interface
To configure your WireGuard server settings, create a configuration file (typically /etc/wireguard/wg0.conf) to define the VPN’s behavior. The interface name (wg0) can be changed if you want to run multiple VPN tunnels (e.g., wg1).
A typical configuration has two main sections:
- [Interface]: This defines the server, so its private key, internal VPN IP, and UDP listen port.
- [Peer]: Each peer (client) you connect adds a block showing their public key and their allowed VPN IP.
Example /etc/wireguard/wg0.conf:
[Interface]
PrivateKey = <client_private_key>
Address = 10.0.0.1/24
ListenPort = 51820 [Peer]
PublicKey = <server_public_key
AllowedIPs = 10.0.0.2/32 - PrivateKey: The server’s private key (do not share).
- Address: Internal VPN IP for the server (use
/24for up to 253 possible peers, e.g.,10.0.0.1/24).
- ListenPort: UDP port (default is
51820; you may change it).
- PostUp: Runs commands after the interface starts. Typically used to set up routing and firewall rules needed for VPN traffic.
- PostDown: Runs commands after the interface stops. Usually cleans up or removes routing and firewall rules that were applied when the VPN started.
- PublicKey: Client’s public key.
- AllowedIPs: Client’s assigned VPN IP (or subnet).
To add more clients, simply repeat the [Peer] section with their own public key and IP address.
After saving your config, secure it by restricting permissions:
sudo chmod 600 /etc/wireguard/wg0.conf This prevents unauthorized access to the contained private key.
Your WireGuard server is now configured. The next step is to secure routing with firewall rules and enable IP forwarding so your VPN clients can communicate through your VPS.
WireGuard Firewall Rules & IP Forwarding
WireGuard firewall rules and WireGuard IP forwarding are critical for enabling VPN clients to route traffic through your server and access the internet. Without these configurations, peers can only communicate directly with the server.
Enable IP Forwarding
First, enable kernel packet forwarding by editing /etc/sysctl.conf:
sudo nano /etc/sysctl.conf Uncomment (remove the # in front) or add these lines. The second is only needed to enable forwarding for IPv4 packages.
net.ipv4.ip_forward=1
net.ipv6.conf.all.forwarding=1 Apply your changes immediately:
sudo sysctl –p Configure Firewall Rules
The firewall setup approach depends on your Linux distribution and complexity needs. Each distribution has a preferred firewall management tool, but all achieve the same goal: allowing WireGuard traffic and enabling NAT for internet access.
Ubuntu (UFW Recommended):
UFW provides a simplified interface for iptables management:
sudo ufw allow 51820/udp
sudo ufw enable For NAT masquerading, edit /etc/ufw/before.rules and insert at the top:
*nat
:POSTROUTING ACCEPT [0:0]
-A POSTROUTING -s 10.0.0.0/24 -o eth0 -j MASQUERADE
COMMIT Replace eth0 with your server’s main interface (check with ip a). Then reload:
sudo ufw reload CentOS/Fedora/Debian (firewalld or iptables):
Modern Red Hat-based systems use firewalld:
sudo firewall-cmd --permanent --add-port=51820/udp
sudo firewall-cmd --permanent --add-masquerade
sudo firewall-cmd --reload Universal iptables (All Distributions):
Direct iptables provides maximum control and consistency:
sudo iptables -A INPUT -p udp --dport 51820 -j ACCEPT
sudo iptables -A FORWARD -i wg0 -j ACCEPT
sudo iptables -t nat -A POSTROUTING -s 10.0.0.0/24 -o eth0 -j MASQUERADECritical Configuration Points
- Port Access: Allow UDP port
51820(or your chosen port) for WireGuard handshakes.
- Interface Forwarding: Enable traffic flow between WireGuard interface (
wg0) and external interface.
- NAT Masquerading: Let VPN clients share your server’s public IP address.
- Interface Names: Replace
eth0with your actual network interface (check withip a).
Making Rules Persistent
Important: iptables rules are lost after reboot. To persist them, do the following:
- Ubuntu/Debian:
sudo apt install iptables-persistent
- CentOS/Fedora:
sudo systemctl enable iptables
- All Systems: Consider PostUp/PostDown commands in the WireGuard config for automatic rule management.
Without these rules, clients might connect to your server but won’t access the internet or your local network.
Why This Configuration Matters
IP forwarding lets your server route packets between different interfaces, while NAT masquerading allows VPN clients to use your server’s public IP when accessing the web. Together, these settings transform your VPS into a proper secure gateway for all WireGuard peers.
Starting and Enabling the WireGuard Service
To bring your VPN online, use wg-quick, which reads your /etc/wireguard/wg0.conf configuration and activates the interface:
sudo wg-quick up wg0 Once started, verify that WireGuard is running and ready to accept connections:
sudo wg show This displays interface status, keys, and (once clients connect) live peer details.
Control and Monitor the Service
For ongoing administration, use systemd commands (which most modern Linux distributions support) to check the active state, manually start, stop, or restart the VPN interface for changes and troubleshooting:
Check the current status:
sudo systemct1 status wg-quick@wg0 Manually start the interface (alternative to wg-quick up):
sudo systemct1 start wg-quick@wg0 Further commands using systemctl stop, reload and restart can help you further control your WireGuard interface.
Enable Autostart at Boot
For reliability, make WireGuard persistent across server reboots:
sudo systemctl enable wg-quick@wg0 This ensures your VPN service is always available without manual intervention, completing the core setup for a robust self-hosted solution.
Verifying the Connection and Adding More Peers
With this WireGuard setup guide nearly complete, the final steps involve testing connectivity and scaling your VPN to support multiple devices. This ensures your server is working correctly and can handle the clients you want to connect.
Creating and Testing Your First Client
Before testing, you’ll need to create a client configuration. Generate keys for the client:
wg genkey | tee client_private.key | wg pubkey > client_public.key Create a client configuration file (e.g., client.conf) that points to your server:
[Interface]
PrivateKey = <client_private_key>
Address = 10.0.0.2/24
DNS = 8.8.8.8 [Peer]
PublicKey = <server_public_key>
Endpoint = <server_public_ip>:51820
AllowedIPs = 0.0.0.0/0
PersistentKeepalive = 25 Key settings explained:
- Endpoint: Your server’s public IP address and WireGuard port
- AllowedIPs: Use 0.0.0.0/0 to route all traffic through the VPN
- PersistentKeepalive: Helps maintain connection through NAT routers
Verify Connectivity
Start the client interface:
sudo wg-quick up client Test the connection with these verification steps:
- Ping the server’s VPN IP:
ping 10.0.0.1
- Check handshake status on server:
sudo wg show
- Verify internet connectivity:
curl ifconfig.me(should show server’s IP)
A successful handshake displays the client’s public key and timestamp in sudo wg show output.
Adding Additional Peers
For each new client, follow this process:
1. Generate unique keys for the new client:
wg genkey | tee client2_private.key | wg pubkey > client2_public.key 2. Add the peer to your server configuration (/etc/wireguard/wg0.conf):
[Peer]
PublicKey = <client2_public_key>
AllowedIPs = 10.0.0.3/32 3. Reload the server configuration:
sudo wg-quick down wg0 && sudo wg-quick up wg0 Scaling Best Practices
- IP Management: Assign each client a unique VPN IP (
10.0.0.2, 10.0.0.3, etc.)
- Organization: Use descriptive file names for client configs (
laptop.conf, phone.conf)
- Security: Each peer must have its own key pair – never reuse keys
- Monitoring: Regularly check
sudo wg showto monitor active connections and data transfer
Troubleshooting Connection Issues
No handshake visible:
- Verify that the firewall rules allow UDP traffic on your chosen port
- Check that the client’s Endpoint setting points to the correct server IP and port
- Ensure both peers have each other’s correct public keys
Handshake successful but no internet access:
- Verify IP forwarding is enabled on the server
- Check NAT/masquerading rules are active
- Confirm that AllowedIPs on the client is set correctly, e.g.,
0.0.0.0/0for full tunnel or custom ranges for split tunneling.
You can explore and calculate these ranges with this helpful tool: WireGuard AllowedIPs Calculator.
- Test with
ping 10.0.0.1first, then external IPs
At this point, your WireGuard VPN supports multiple clients with secure, encrypted connections. Each peer can safely access the internet through your VPS, completing your self-hosted VPN infrastructure.
WireGuard VPS FAQ
What is WireGuard?
WireGuard is a modern VPN protocol designed to be faster, simpler, and more secure than older options like OpenVPN or IPSec.
Can I manage WireGuard with a graphical interface?
Yes. While WireGuard is typically managed via the command line, there are third-party tools like wg-dashboard that offer a web-based interface for easier management. These panels let you view peers, generate configuration files, and control your server without needing to run complex terminal commands – making WireGuard much more accessible, especially for beginners.
How does WireGuard work?
It uses lightweight code and state-of-the-art cryptography to create encrypted tunnels between devices. Each peer is identified by a public key, ensuring only authorized connections. A more detailed description can be found on the official WireGuard website.
What is the WireGuard VPN protocol?
The WireGuard VPN protocol defines how encrypted traffic is established and transmitted over UDP, optimized for speed and low latency.
What is the difference between VPS and VPN?
A VPS is your own virtual server for hosting projects and apps, while a VPN encrypts your online traffic for privacy. Learn more in the Contabo guide here.
How to set up WireGuard?
Install WireGuard tools, generate key pairs, configure the server interface, apply firewall rules, and add clients. This guide covers the complete process step-by-step.
How to install WireGuard?
On Ubuntu/Debian: sudo apt install wireguard -y. On Fedora/CentOS: sudo dnf install wireguard-tools. Then create /etc/wireguard/wg0.conf with your server and peer settings.
How do I check if WireGuard is working?
Run sudo wg show on the server. A successful handshake displays the peer’s public key and latest connection timestamp.
