In the rapidly evolving digital landscape, the need for secure and private communication on the internet has become more crucial than ever. This is where SSL (short for: Secure Sockets Layer) comes into play. SSL is a fundamental technology that ensures encrypted connections between web servers and browsers. This is archived by safeguarding sensitive information like passwords and protecting users from cyber threats. In this comprehensive guide, we will explore the world of SSL, its historical context, and its significance in modern web usage.
SSL, first introduced by Netscape in 1994, revolutionized the way data is transmitted over the internet. It provided a secure layer of encryption, making it increasingly difficult for attackers to intercept and decipher sensitive information exchanged between users and websites. Over the years, SSL has evolved into Transport Layer Security (TLS), encompassing newer versions and stronger cryptographic algorithms to enhance security.
Understanding the Importance of SSL
The importance of understanding SSL cannot be overstated. As an internet user, it is crucial to comprehend how SSL works, its role in protecting personal and financial data, and its impact on trust and website credibility. For website owners, developers, and administrators, having a thorough understanding of SSL is essential for implementing proper security measures. This can be used to meet compliance requirements, and instilling confidence in visitors.
Through this ultimate guide to SSL, you will gain a comprehensive understanding of SSL, its significance, and its practical implementation. We will explore the inner workings of SSL. This includs the SSL handshake process, the role of SSL certificates, and the different types of certificates available. We will delve into the benefits SSL provides, such as protecting sensitive information, enhancing customer trust, and improving search engine rankings. Furthermore, we will address common misconceptions and debunk SSL myths.
By the end of this guide, you will be equipped with the knowledge necessary to make informed decisions regarding SSL implementation. This also means website security, and safeguarding their online presence. Whether you are a website owner, a developer, or simply an internet user concerned about privacy and security, this guide will empower you to navigate the SSL landscape confidently.
Understanding SSL
SSL: A Secure and Encrypted Connection
SSL, also known as Secure Sockets Layer, is a cryptographic protocol that establishes a secure and encrypted connection between a web server and a user’s web browser. It acts as a virtual “security blanket” for internet traffic, ensuring that data transmitted between the server and the browser remains confidential and protected from unauthorized access.
Encryption: Safeguarding Data
The primary role of SSL is to encrypt the information exchanged between the server and the browser, making it unreadable to anyone attempting to intercept the data. Encryption is achieved through the use of cryptographic algorithms, which transform the data into a format that can only be deciphered with the appropriate decryption key.
Observing SSL in Action
You can even observe how SSL encrypts data by extracting some packets using a network tool.
In our example our username is: [email protected]
and our password is: “unencryptedpassword”
Without any encryption (without SSL) our credentials can be easily extracted as you can see here:
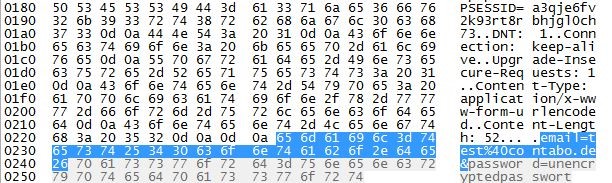
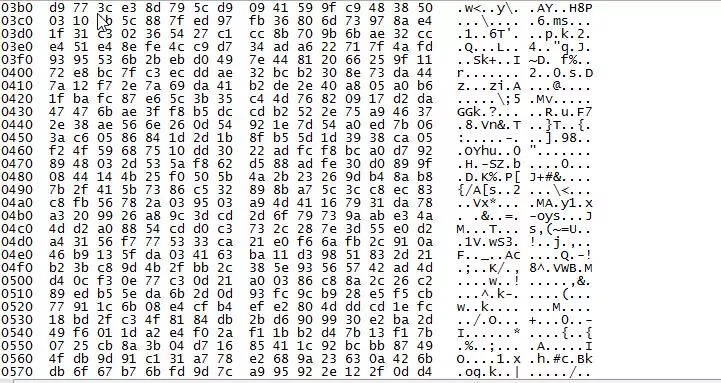
But if we use a secure connection by using SSL we cannot extract the credentials:
SSL Certificates: Ensuring Trust and Security
SSL certificates play a crucial role in ensuring the authenticity and integrity of communication. Issued by trusted Certificate Authorities (CAs), these certificates serve as digital passports that verify the identity of the website or server. Users’ browsers check the SSL certificate’s validity and trusted CA during the connection process, establishing trust between the user and the server.
HTTPS: Indicating Secure Connections
SSL certificates enable the use of HTTPS (Hypertext Transfer Protocol Secure) in website URLs. The “https://” prefix indicates that the website is secured with SSL, providing an additional layer of assurance to users that their connection is encrypted and their data is secure.
Vital Defense Against Threats
SSL acts as a vital defense against various threats, such as eavesdropping, data tampering, and identity theft. By encrypting internet traffic, SSL prevents attackers from intercepting sensitive information, ensuring it remains encrypted and unreadable even if accessed.
Understanding SSL’s Importance
Understanding SSL is essential for website administrators and developers. Implementing SSL and using SSL certificates helps protect users’ information, build trust and credibility, and enhance overall online security.
In the next section, we will delve deeper into the specific roles and importance of SSL, exploring how it protects sensitive information, enhances customer trust, and provides SEO benefits.
The Role and Importance of SSL
SSL plays a multifaceted role in the realm of internet security, offering a range of benefits that are crucial in today’s digital landscape:
Protection of Sensitive Information
One of the primary roles of SSL is to protect sensitive information transmitted over the internet. By encrypting data during transmission, SSL ensures that confidential details, such as login credentials, credit card numbers, and personal information, cannot be intercepted and deciphered by malicious actors. This protection extends to various online activities, including e-commerce transactions, online banking, and data submissions on websites.
Enhancing Customer Trust
SSL plays a significant role in building trust and confidence among website visitors. When users visit a website secured with SSL, they are presented with visual indicators, such as a padlock symbol and the “https://” prefix in the address bar:
These indicators assure users that their connection is secure and that the website has taken measures to protect their data. This trust-building aspect is particularly vital for e-commerce websites, where customers need reassurance that their sensitive information will remain private and secure. We at Contabo of course offer an SSL-secured website to make sure every transaction on our website is secure!
SEO Benefits
Search engines prioritize secure websites in their search results. Implementing SSL on a website can positively impact its search engine rankings. Search engine algorithms take into account SSL as a ranking factor, promoting secure websites over non-secure ones. By investing in SSL, website owners can improve their visibility in search engine results and attract more organic traffic which could lead to more revenue on e.g. a web shop or a website which makes money using ads.
Prevention of Cyberattacks like Phishing and Man-in-the-Middle Attacks
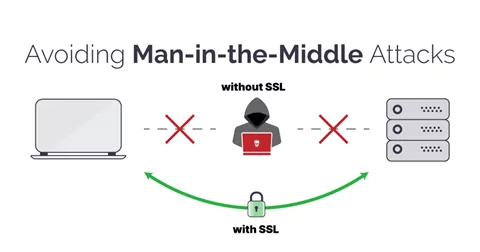
SSL acts as a shield against various cyber threats, including phishing and man-in-the-middle attacks. Phishing attacks involve tricking users into revealing sensitive information by posing as legitimate entities. SSL prevents attackers from intercepting data during transmission and ensures that users are communicating securely with the intended website, reducing the risk of falling victim to phishing scams. Similarly, SSL safeguards against man-in-the-middle attacks, where attackers intercept and alter communication between users and websites. By encrypting the data, SSL mitigates the risk of unauthorized manipulation and maintains the integrity of the transmitted information.
Requirement for HTTPS and Regulatory Compliance
The use of HTTPS, enabled by SSL, is becoming increasingly important and even mandatory in certain contexts. For instance, many web browsers now display warnings when users attempt to access non-secure websites, discouraging interaction due to potential security risks.
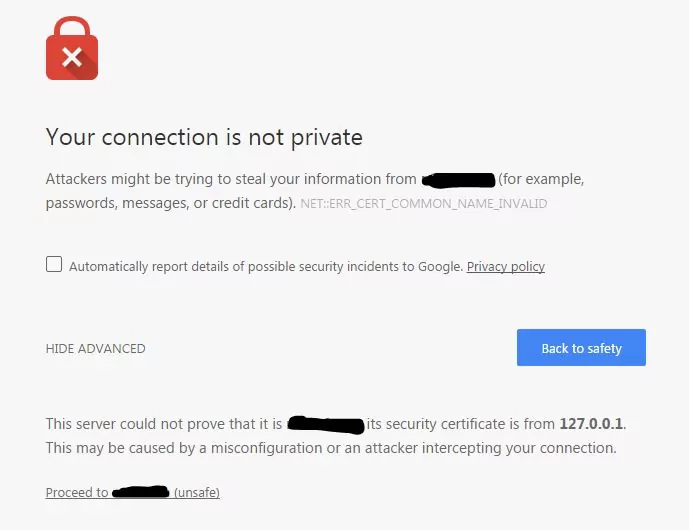
Furthermore, regulatory bodies and industry standards, such as the General Data Protection Regulation (GDPR), Payment Card Industry Data Security Standard (PCI DSS), and Health Insurance Portability and Accountability Act (HIPAA), require the use of SSL for handling sensitive data. Complying with these regulations is crucial for businesses operating in various sectors and ensures the protection of user privacy and data security.
Understanding the role and importance of SSL empowers website owners, administrators, and users to prioritize online security, protect sensitive information, and navigate the ever-changing landscape of regulatory requirements.
In the next section, we will explore how SSL works, diving into the intricate processes of the SSL handshake, encryption, and the role of SSL certificates and certificate authorities.
How SSL Works
SSL operates through a complex series of processes and protocols to establish a secure and encrypted connection between a web server and a user’s web browser. Understanding the inner workings of SSL is crucial to grasp how it provides secure communication.
Explanation of SSL Handshake Process
The SSL handshake is the initial phase of establishing a secure connection. During this process, the client (web browser) and the server exchange information to authenticate each other, negotiate the encryption algorithms to be used, and generate session keys for secure communication. The handshake involves the following steps:
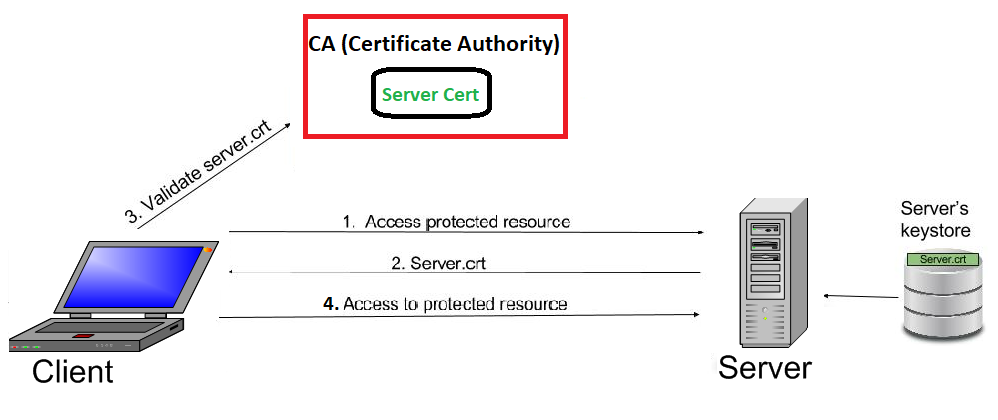
1. The Client requests some protected data from the server on HTTPS protocol. This initiates SSL/TLS handshake process.
2. Now the Server returns its public certificate to the client along with server hello message.
3. The Client validates/verifies the received certificate. Client verifies the certificate through certification authority (CA) for CA signed certificates.
4. SSL/TLS client sends the random byte string that enables both the client and the server to compute the secret key to be used for encrypting subsequent message data. The random byte string itself is encrypted with the server’s public key.
5. After agreeing on this secret key, client and server communicate further for actual data transfer by encrypting/decrypting data using this key.
Discussing Key Terms: Public Key, Private Key, and Encryption
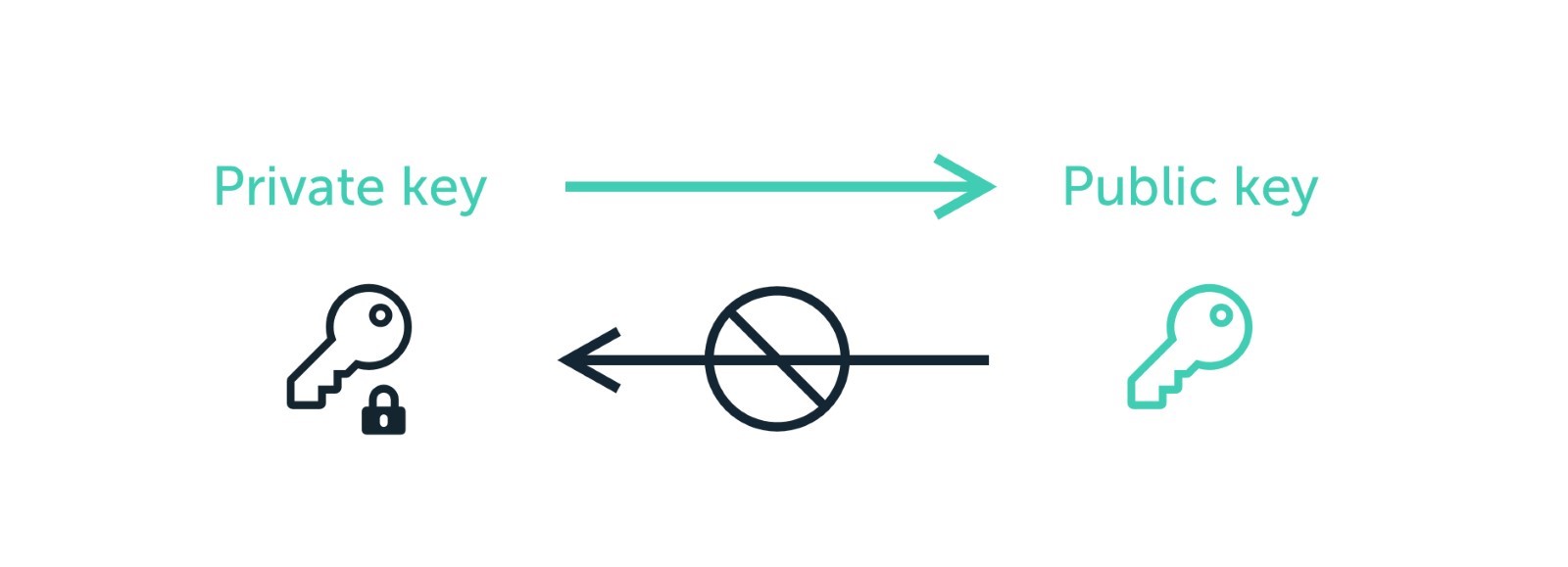
SSL relies on asymmetric encryption, also known as public-key encryption. In this encryption scheme, two types of keys are used: a public key and a private key. The public key is used to encrypt data, while the corresponding private key is used for decryption.
When a user connects to a secure website, the server’s SSL certificate contains its public key. The client uses this public key to encrypt the session key, ensuring that only the server, with its corresponding private key, can decrypt and access the session key. Once the session key is exchanged securely, symmetric encryption is used for efficient and secure data transfer.
Explanation of SSL Certificates and Certificate Authorities
SSL certificates play a crucial role in verifying the authenticity of the server and establishing trust between the client and the server. These certificates are issued by Certificate Authorities (CAs), trusted entities responsible for verifying the identity of the server and binding it to a specific domain.
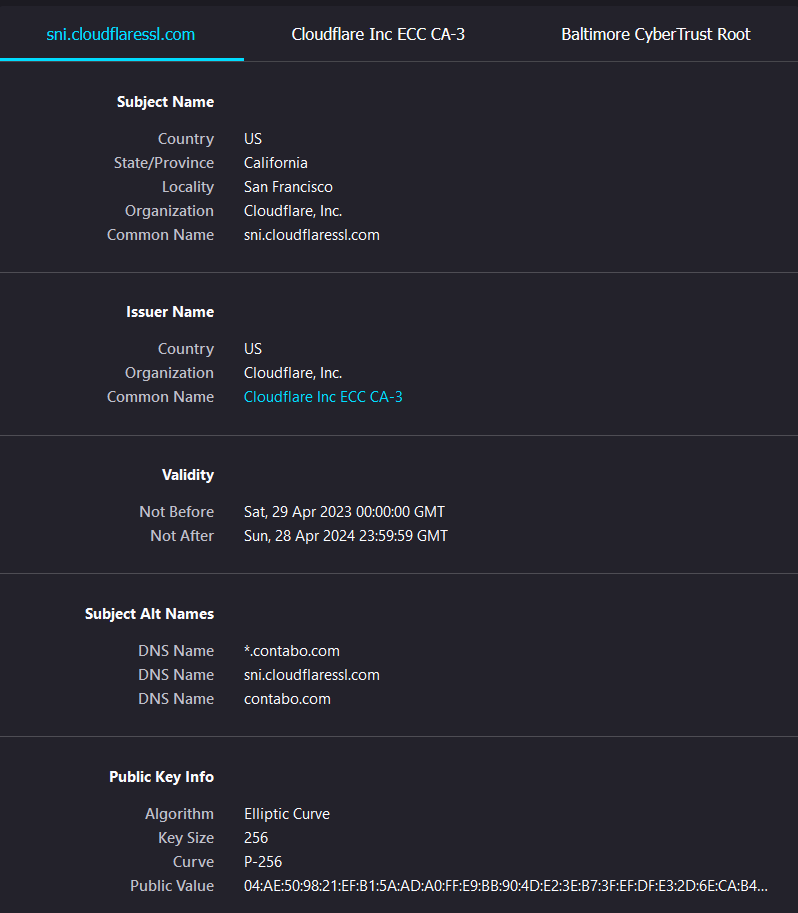
SSL certificates contain information such as the domain name, the certificate’s expiration date, the public key, and the CA’s digital signature. The digital signature ensures that the certificate has not been tampered with and can be trusted. The client’s web browser checks the SSL certificate’s validity and the CA’s trustworthiness to ensure a secure connection.
The certificate for contabo.com looks like this:
SSL/TLS Protocol Layers
SSL operates within the broader context of the SSL/TLS protocol layers. The Transport Layer Security (TLS) protocol is an updated version of SSL. TLS consists of two primary layers: the TLS Record Protocol and the TLS Handshake Protocol.
The TLS Record Protocol ensures secure and reliable data transport through encryption and integrity checks. It takes data from higher-level protocols, divides it into manageable chunks called TLS records, encrypts them, and sends them to the other end.
The TLS Handshake Protocol, as discussed earlier, facilitates the SSL handshake process. It establishes the encrypted connection, verifies the server’s identity, and negotiates encryption algorithms and session keys.
By understanding the SSL handshake process, the role of public and private keys, the importance of SSL certificates, and the broader TLS protocol layers, one gains insight into how SSL provides secure communication over the internet.
In the next section, we will explore different types of SSL certificates and their characteristics, enabling readers to choose the most suitable certificate for their specific needs.
Types of SSL certificates
SSL certificates are available in different types, offering varying levels of validation and features. Let’s explore the three main types of SSL certificates and discuss their pros and cons:
TL; DR:
If you are too lazy to read all of this need a cheat-sheet for the future: Here is a table giving you a brief description and a summary of all the pros and cons of every certificate type:
| SSL Certificate Type | Description | Pros | Cons |
| Domain-Validated (DV) | Basic SSL certificates verifying domain ownership. | – Easy and quick issuance, suitable for small websites or blogs. – Cost-effective, accessible to individuals/businesses | – Limited validation, offering minimal assurance. – Limited trust indicators may impact user confidence. |
| Organization-Validated (OV) | SSL certificates verifying organization identity and domain. | – Enhanced trust with verified organization information. – Additional security features (e.g., SAN certificates). | – Longer validation process, taking a few days or more. – Higher cost compared to DV certificates due to additional steps and trust indicators. |
| Extended Validation (EV) | SSL certificates offering the highest level of validation. | – Highest level of trust with “green address bar” display. – Comprehensive validation, boosting user confidence. | – Lengthy validation process, several days or weeks. – More expensive compared to DV and OV certificates due to extensive verification and trust indicators. |
Domain-Validated Certificates (DV)
Domain-validated certificates are the most basic type of SSL certificates. They verify the ownership of the domain and ensure that the certificate is issued to the correct entity. The validation process typically involves confirming domain control through email verification or domain DNS record changes.
Pros:
Easy and quick issuance: DV certificates can be obtained and issued within minutes or hours, making them ideal for small websites or personal blogs.
Cost-effective: DV certificates are usually the most affordable option, making them accessible for individuals and small businesses.
Cons:
Limited validation: DV certificates provide the lowest level of assurance. They only verify domain ownership, offering minimal information about the organization behind the website.
Limited trust indicators: DV certificates may not display the organization’s name in the browser’s address bar, which may impact user trust.
Organization-Validated Certificates (OV)
Organization-validated certificates go beyond domain validation to verify the identity of the organization. The CA validates both the domain ownership and organizational details, such as company name and address, to issue the certificate.
Pros:
Enhanced trust: OV certificates display verified organization information, providing users with increased assurance about the authenticity of the website.
Additional security features: OV certificates often include higher encryption levels and support for advanced features like SAN (Subject Alternative Name) certificates, which allow multiple domains to be secured under a single certificate.
Cons:
Longer validation process: Obtaining an OV certificate requires more thorough verification, which can take a few days or longer, depending on the organization’s documentation and responsiveness.
Higher cost: OV certificates are typically more expensive than DV certificates due to the additional validation steps and increased trust indicators.
Extended Validation Certificates (EV)
Extended Validation certificates offer the highest level of validation and are recognized by the prominent “green address bar” in most browsers. They provide the most extensive verification process, including legal, physical, and operational checks of the organization.
Pros:
Highest level of trust: EV certificates provide the strongest visual assurance to users with the distinct green address bar, indicating a highly secure and trusted website.
Comprehensive validation: EV certificates involve rigorous validation procedures, establishing the legitimacy of the organization, which can enhance user confidence and trust.
Cons:
Lengthy validation process: Obtaining an EV certificate involves a comprehensive verification process, which can take several days or weeks to complete.
Higher cost: EV certificates tend to be more expensive compared to DV and OV certificates due to the in-depth validation process and additional trust indicators.
Choosing the right type of SSL certificate depends on the specific needs and requirements of your website. While DV certificates offer basic encryption and quick issuance, OV and EV certificates provide higher levels of trust and extended validation. Consider the nature of your website, the sensitivity of the data being transmitted, and the level of trust you want to establish with your visitors when selecting an SSL certificate.
In the next section, we will explore the process of installing an SSL certificate. We will provide a step-by-step instructions for popular web hosts and servers, ensuring a smooth implementation of SSL on your website.
How to install an SSL Certificate
Implementing SSL on your website requires proper installation of an SSL certificate. In this section, we will provide a step-by-step guide for installing an SSL certificate on popular web hosts. Moreover we will discuss SSL installation for different server types, highlight the role of Certificate Authorities (CAs), and troubleshoot common SSL installation issues.
cPanel:
a. Log in to your cPanel account.
b. Navigate to the “SSL/TLS” section.
c. Generate a Certificate Signing Request (CSR) and private key.
d. Submit the CSR to your chosen CA and obtain the SSL certificate.
e. Return to cPanel and install the SSL certificate.
f. Enable HTTPS redirection to ensure all traffic uses the secure connection.
Plesk:
a. Access your Plesk control panel.
b. Go to the “SSL/TLS Certificates” section.
c. Click “Add SSL/TLS Certificate” and fill in the required information.
d. Submit the CSR to your CA and receive the SSL certificate.
e. Upload and install the SSL certificate in Plesk.
f. Configure the website to use the SSL certificate.
Apache2 (manual):
a. Generate a CSR and private key using OpenSSL or a control panel.
b. Submit the CSR to the CA and obtain the SSL certificate.
c. Configure Apache to use the SSL certificate by updating the virtual host file.
d. Restart the Apache server for the changes to take effect.
Apache2 (Certbot + Lets Encrypt)
Find out more about Lets Encrypt in our dedicated article here.
a. Install Certbot
sudo apt install certbot python3-certbot-apache b. Stop Apache2
systemctl stop apache2 c. Generate a certificate
certbot --apached. Start Apache2
systemctl start apache2 e. Enable Auto-Renew
certbot renew --dry-run Nginx:
a. Generate a CSR and private key.
b. Obtain the SSL certificate from the CA using the CSR.
c. Configure Nginx to use the SSL certificate by modifying the server block configuration.
d. Restart or reload the Nginx service.
The Role of Certificate Authorities (CAs) in SSL Installation
Certificate Authorities play a crucial role in the SSL installation process. They are trusted entities that issue SSL certificates to verify the identity of the website. The CA validates the certificate applicant’s ownership or control of the domain before issuing the certificate. Once obtained, the SSL certificate is installed on the server to enable secure communication with users’ browsers.
Troubleshooting Common SSL Installation Issues
Certificate Mismatch: Ensure that the domain in the SSL certificate matches the domain used to access the website.
Intermediate Certificate: Verify if the correct intermediate certificate(s) are installed, as missing intermediates can cause SSL errors.
Mixed Content: Check for mixed content warnings, as insecure elements (HTTP) on secure pages (HTTPS) can trigger browser warnings.
Certificate Chain Issues: Ensure that the SSL certificate is properly chained to the root CA certificate.
Key and File Permissions: Set appropriate permissions for private keys and SSL certificate files to avoid permission-related errors.
It is important to follow the specific instructions provided by your web host or server documentation when installing an SSL certificate. Additionally, consult the documentation of your chosen CA for any specific guidelines related to SSL installation.
In the next section, we will explore the impact of SSL on web browsers. This includes how browsers display secure sites and SSL-related warnings. We will also cover the consequences of not having an SSL certificate on browser display.
SSL and Web Browsers
SSL plays a significant role in how web browsers display and interact with websites. In this section, we will explore how browsers indicate secure sites. Moreover we will discuss browser warnings related to SSL, and understand the impact of not having an SSL certificate on browser display.
How Browsers Display Secure Sites
When a website is secured with SSL, modern web browsers provide visual indicators to inform users that their connection is secure. These indicators vary across different browsers but commonly include:

A padlock symbol in the address bar
The “https://” prefix in the URL
A green address bar (for Extended Validation certificates)
These visual cues assure users that their connection is encrypted and that the website they are visiting has undergone verification to ensure its authenticity.
Understanding Browser Warnings Related to SSL
Web browsers may display warning messages when encountering issues with SSL certificates or when attempting to access non-secure (HTTP) sites. Some common browser warnings include:
Certificate Error: This warning indicates that the SSL certificate presented by the website is invalid, expired, or issued by an untrusted Certificate Authority. Users should proceed with caution or avoid accessing the site.
Mixed Content Warning: Browsers display this warning when a secure (HTTPS) page contains insecure (HTTP) elements, such as images or scripts. The warning alerts users that the page is not fully secure, potentially exposing their data to interception or manipulation.
Not Secure Warning: Starting with certain browser versions, sites without an SSL certificate or using HTTP are labeled as “Not Secure.” This warning aims to inform users that the connection is not encrypted, potentially leaving their data vulnerable to interception.
The Impact of Not Having an SSL Certificate on Browser Display
Not having an SSL certificate can have several negative implications for browser display and user experience. Without an SSL certificate:
- Browsers may display warnings indicating that the website is not secure or that the connection is not private.
- The absence of SSL can lead to a lack of trust from users, causing them to abandon the website or hesitate to share sensitive information.
- Search engines, such as Google, consider SSL as a ranking factor, and non-secure sites may experience lower visibility in search results.
- Websites without SSL may not be compatible with new browser features and technologies, limiting their functionality and user experience.
To provide a secure browsing experience, gain user trust, and ensure compatibility with modern web technologies, it is essential to have a valid SSL certificate installed on your website.
In the next section, we will debunk common myths and misunderstandings surrounding SSL, providing clarity on its capabilities and limitations.
SSL Myths and Misunderstandings
While SSL technology has been widely adopted and implemented, there still exist common misconceptions and misunderstandings surrounding its capabilities and limitations. In this section, we will debunk some of these misconceptions and shed light on the limitations of SSL.
Debunking Common Misconceptions about SSL
SSL is only necessary for e-commerce websites: While SSL is crucial for securing sensitive information during e-commerce transactions, it extends beyond e-commerce websites alone. Any website that handles user data, such as login credentials, contact forms, or personal information, can benefit from SSL encryption.
SSL guarantees complete website security: While SSL provides encryption for data in transit, it does not guarantee the security of the entire website. SSL does not protect against vulnerabilities in the web application itself or server-side security issues. Regular security measures, such as software updates, strong passwords, and secure coding practices, are also necessary to ensure comprehensive website security.
SSL certificates are all the same: SSL certificates differ in terms of validation level, features, and trust indicators. Domain-validated (DV) certificates provide basic encryption, while organization-validated (OV) and extended validation (EV) certificates offer higher levels of validation and trust indicators like the green address bar.
The Limitations of SSL
SSL only protects data in transit: SSL encryption secures data during transmission between the server and the user’s browser. However, it does not protect data on the server or user devices. Additional measures, such as secure storage practices and user-side security measures, are necessary to protect data at rest and in the user’s environment.
SSL cannot protect against all cyber threats: While SSL helps protect against eavesdropping and tampering with data in transit, it does not provide comprehensive protection against all cyber threats. SSL cannot prevent attacks such as distributed denial-of-service (DDoS) attacks, server-side vulnerabilities, or social engineering attacks. A holistic approach to security, including multiple layers of protection, is necessary to address various threat vectors.
SSL does not guarantee the trustworthiness of a website: SSL certificates establish trust in the encryption and authenticity of a website. However, they do not guarantee the trustworthiness of the website’s content or the intentions of its operators. Users should exercise caution and verify the reputation and credibility of the website and its operators beyond SSL indicators.
Understanding the realities of SSL technology and its limitations is vital for making informed decisions about website security and implementing comprehensive security measures.
In the next section, we will explore the future of SSL and internet security, including the evolution of SSL and the emergence of the newer version, TLS (Transport Layer Security). We will also discuss possible future changes in the landscape of internet security.
The future of SSL and Internet security
As technology continues to advance and cyber threats evolve, the world of SSL and internet security must also adapt. In this section, we will explore the evolution of SSL. This includes the emergence of TLS (Transport Layer Security) as its newer version, and discuss possible future changes in the landscape of internet security.
The Evolution and Adaptation of SSL
SSL has evolved significantly since its inception, with newer versions addressing vulnerabilities and improving security. The most widely used version today is TLS, which is based on SSL protocols and provides enhanced security features. SSL/TLS implementations have become more robust, supporting stronger encryption algorithms, better key exchange mechanisms, and improved certificate management.
Discuss the Newer Version of SSL – TLS (Transport Layer Security)
TLS, the successor to SSL, builds upon the foundations of SSL to provide secure communication on the internet. This is archived by offering stronger encryption algorithms, improved authentication mechanisms, and enhanced protection against various security threats. TLS versions, such as TLS 1.2 and TLS 1.3, have introduced significant advancements in security and performance, addressing vulnerabilities found in earlier SSL versions.
The Possible Future Changes in the World of Internet Security
Quantum-Safe Encryption: As quantum computers become more powerful, there is a growing need for quantum-safe encryption algorithms. Future SSL/TLS implementations may incorporate quantum-resistant encryption to ensure secure communication in a post-quantum computing era.
Increased Automation and Artificial Intelligence (AI): Automation and AI technologies can play a significant role in enhancing internet security. AI-powered systems can detect and mitigate security threats in real-time, providing proactive defense against emerging attacks.
Improved Certificate Transparency: The Certificate Transparency (CT) initiative aims to make SSL certificate issuance and revocation more transparent. In the future, CT may become a standard practice, ensuring better accountability and increasing trust in the certificate issuance process.
Enhanced Authentication Mechanisms: Stronger authentication mechanisms, such as multi-factor authentication and biometric authentication, may become more prevalent to enhance the security of SSL/TLS connections and protect against unauthorized access.
Integration with Emerging Technologies: SSL/TLS may integrate with emerging technologies such as Internet of Things (IoT), blockchain, and cloud computing, ensuring secure and encrypted communication in these domains.
Regulatory and Compliance Developments: Changes in regulatory frameworks and compliance requirements will likely shape the future of SSL and internet security. Stricter data protection regulations and increased emphasis on privacy may drive further adoption of SSL/TLS to ensure compliance.
As the digital landscape continues to evolve, SSL and internet security will adapt to meet new challenges and threats. The future will witness advancements in encryption, authentication, automation, and integration with emerging technologies to provide robust and secure internet communication.
Conclusion
In today’s digital world, SSL (Secure Sockets Layer) remains an essential technology for ensuring secure and private communication on the internet. Throughout this guide, we have explored the significance of SSL, its historical context, and its role in modern web usage. Let’s recap the importance of SSL and conclude with final thoughts on its role in ensuring safe internet browsing.
SSL’s Crucial Role in Protecting Sensitive Information
SSL is crucial for protecting sensitive information transmitted over the internet. By encrypting data in transit, SSL shields user data from eavesdropping, tampering, and identity theft. Whether it’s personal information, financial details, or login credentials, SSL ensures that this data remains confidential and secure.
Enhancing Customer Trust and Security
Moreover, SSL enhances customer trust by providing visual indicators of a secure connection, such as the padlock symbol and the “https://” prefix in the browser’s address bar. These indicators build confidence in users and reassure them that their data is securely transmitted
Additional Benefits of SSL
Beyond protecting sensitive information, SSL offers additional benefits. It positively impacts search engine rankings, as search engines prioritize secure websites in their search results. SSL also helps prevent cyberattacks like phishing and man-in-the-middle attacks, safeguarding users from falling victim to malicious schemes. Furthermore, SSL is not only essential for security but also for regulatory compliance. Many data protection regulations, such as GDPR, PCI DSS, and HIPAA, require the use of SSL to protect sensitive data and ensure regulatory compliance.
In conclusion, SSL plays a vital role in ensuring safe internet browsing. It protects sensitive information, enhances customer trust, improves search engine rankings, prevents cyberattacks, and meets regulatory requirements. By implementing SSL, website owners and administrators contribute to a safer and more secure online environment for their users.
Future Outlook
As the digital landscape continues to evolve, SSL will adapt and evolve alongside it. The emergence of TLS as the newer version of SSL, advancements in encryption algorithms, integration with emerging technologies, and increasing focus on privacy and data protection will shape the future of SSL and internet security.
In this ever-changing digital era, understanding and implementing SSL is crucial for safeguarding online communication. Also its important for protecting user data, and building trust with website visitors. By prioritizing SSL, we contribute to a safer and more secure internet for all.