Losing access to your system, whether it is the main password for Linux or Windows, can be incredibly frustrating and risky. It can disrupt your work and put your data at risk. We know how important this is, and we are here to guide you through the process of recovering your password.
Before we take it step by step, let’s mention that prevention is just as important as recovery. To help you keep your passwords organized and your digital life secure, we also have a guide on how to install Bitwarden on a VPS. Bitwarden is a popular password manager that can make your life a lot easier when it comes to managing passwords. So, let us get started and help you control your digital security.
How to Create a Secure Password
Whether safeguarding personal accounts or critical business systems, how secure your passwords are is a cornerstone of digital protection. In the following section, we will give you essential tips for creating secure passwords, offering practical guidance to enhance your online security.
- Complexity: Create a password that includes a combination of upper and lower-case letters, numbers, and special characters to increase complexity.
- Length: Aim for a password that is at least 12 to 16 characters long, or even longer for enhanced security.
- Avoid Common Patterns: Avoid using easily guessable information such as common words, phrases, or easily predictable patterns.
- Uniqueness: Never reuse passwords across multiple accounts or systems. Each password should be unique to prevent potential security breaches.
To test the security of your password, you can use a website like How Secure Is My Password. This tool generates an estimate of how long it would take for a computer to crack your password, helping you test its strength.
There are also tools which will help you create a secure password, for example the Strong Password Generator on the Bitwarden website.
By following these password security recommendations and using such tools, you can significantly enhance the security of your server and thus protect sensitive data from potential threats.
With the guideline for creating secure passwords in place, let’s also look at how to reset System Passwords in various OSs.
Resetting Linux Root Password
If you find yourself locked out of your Linux system due to a forgotten root password, do not panic – there are several ways to regain access. Below, we will explore two methods for resetting the Linux root password:
Option 1: Using the Contabo Customer Control Panel (CCP)
If you are a Contabo customer, resetting your Linux root password is a straightforward process through the Contabo Customer Control Panel (CCP). Here is how:
1. Log in to your Contabo Customer Control Panel (CCP) using your customer credentials.
2. Navigate to the menu on the left and click on “Your Services”.
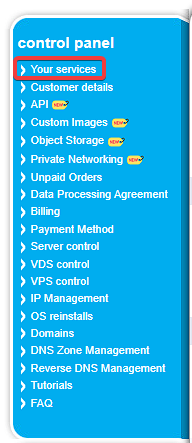
3. Now hover over the “Manage” button next to the server you want to perform a password reset on and click on “Control”.
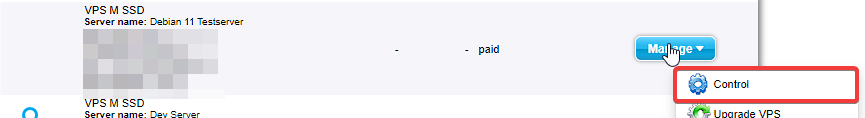
4. Hover over the “Manage” button for the corresponding server again and select “Password reset”.
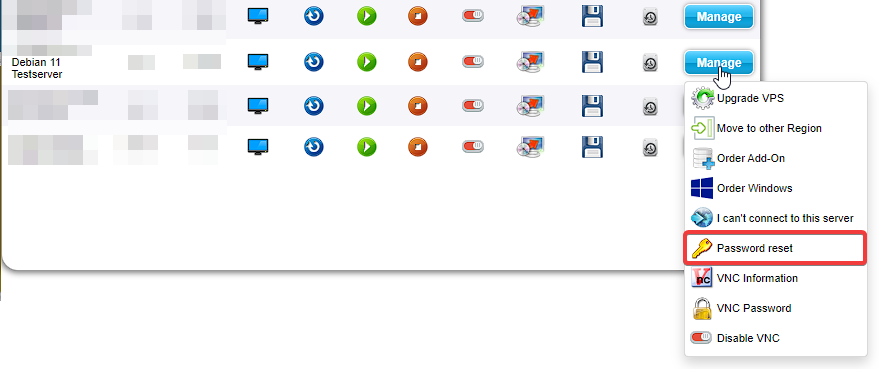
5. Create a new root password in the menu that opened. Then, click on “Perform password reset”.
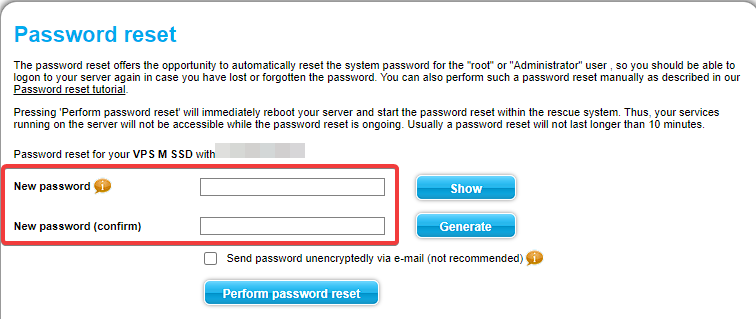
After a few minutes, your password has been reset and your server rebooted. You will now be able to login via SSH with your new root password.
Option 2: Manual Reset via Rescue Mode
If you are not a Contabo customer or prefer a manual approach, you can reset the Linux root password by using Rescue Mode. Here is a step-by-step guide on how to do it:
1. Access your server’s hosting provider dashboard or control panel. Most providers offer a feature called “Rescue Mode” or “Recovery Mode.” Activate it for your server.
If you are a Contabo Customer, go to the Customer Control Panel (CCP) and select “Your Services” in the left menu bar.
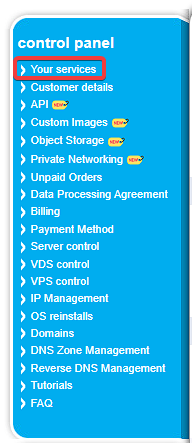
Now hover over the “Manage” button and select “Rescue System”
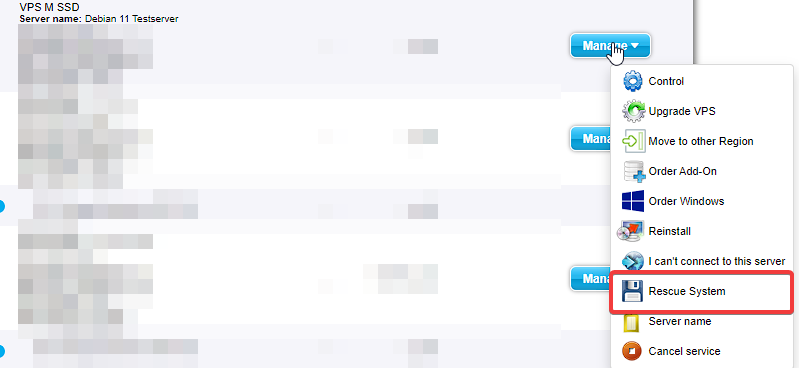
In the following menu leave the “Rescue System Version” on “Debian Rescue (Recommended)” and create a password for the Rescue instance.
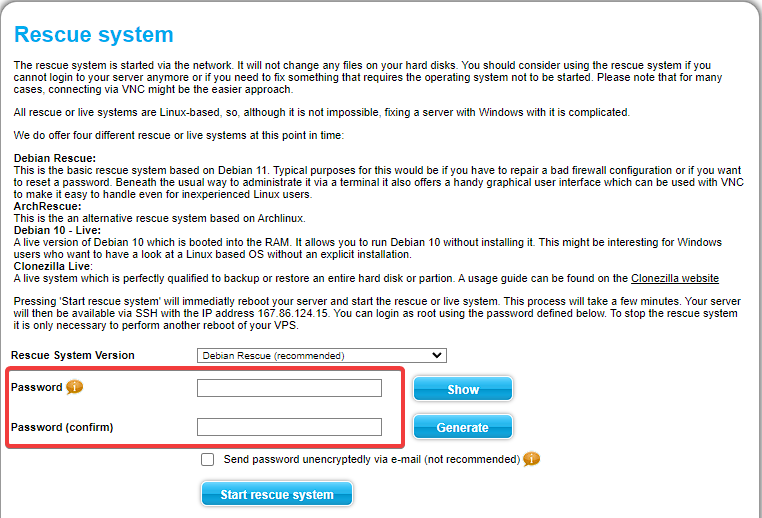
Finish this process by clicking on “Start rescue system”.
3. Once your server is in Rescue Mode, you will receive instructions on how to access it. This usually involves using SSH or a web-based console provided by your hosting provider. If you are a Contabo Customer, just use the IP address of the server with the password you created in the step above to connect to your server via SSH.
4. Now you need to mount the system partition. To do so, list all partitions on the server by using this command:
fdisk –l On our test server the output looks like this:
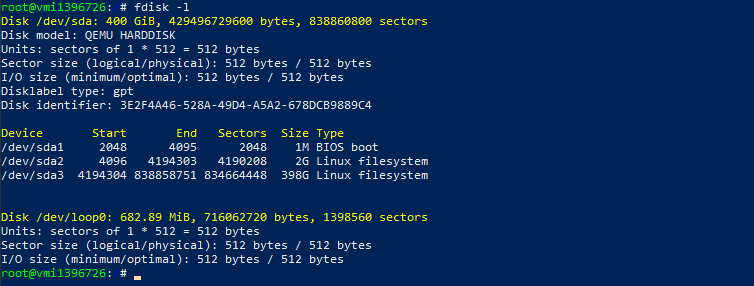
Identifying the actual system partition is not always easy. In our case /dev/sda3 is the system partition that needs to be mounted. To check it use the following commands:
mount [device] /mnt cd /mnt ls If the output of the ‘ls’ command displays the familiar Linux filesystem structure as shown below, you have successfully mounted the correct partition.
If the output is different, use this command to unmount the wrong partition:
umount /mnt Repeat this process until you have found the right partition.
Once you mounted the right partition, use this command to login into it:
chroot /mnt /bin/bashNow execute the following command to change the root password:
passwd rootAfter confirming the new password by entering it twice, your password has been updated successfully and you can leave the whole session by using this command:
exitDo not forget to unmount the partition again with this command:
umount /mntResetting the Windows Server Administrator Password
Resetting the administrator password on a Windows server system is not as straightforward as on a Linux server due to enhanced security and safety features from Microsoft. These features are designed to protect your server from unauthorized access, even in the event of a lost password. Here, we will explain why direct password resets are challenging and offer an alternative approach:
Why Doesn’t Microsoft Allows to Reset the Administrator Password?
Modern Windows Server versions employ robust security measures to safeguard your data and system integrity. These include encryption of stored passwords and account lockout policies. As a result, the Windows Administrator password cannot be reset to prevent unauthorized access and potential security breaches.
Alternative Approach: Recovering Files and Reinstalling Windows Server
To regain access to a Windows Server system when the Administrator password is lost or inaccessible, the recommended approach is to recover essential files and then reinstall Windows Server. This involves creating backups of important data, reinstalling the operating system, and then restoring your data.
For a comprehensive, step-by-step guide on how to recover files and reinstall Windows Server with a new Administrator password, check out our detailed article on How to Recover Files after losing the Admin Password in Windows Server 2019/2022. This guide provides in-depth instructions, tips, and best practices to help you navigate this complex process safely and efficiently.
Conclusion
In the world of digital security, taking care of your system passwords is super important, regardless of whether you are using Linux or Windows. Losing access to your system can turn into a big headache.
By following the steps described in this article, you can safely regain access to your system. Also, think about using a password manager to help you manage your passwords better. In simple terms, looking after your passwords is not about convenience; it is a key part of keeping your digital world safe. So, make it a priority!